Week in OSINT #2023-17
After a week off, I'm back with several topics ranging from geolocation, Tweetdeck, a streaming platform and some OpSec tips.
Two weeks ago I knew my week was fully planned, so there wouldn't be time to publish an episode, so I chose to take some time off. For this week, I have some cool topics to talk about, but one thing I do urge you to read, is the first section about Atlas OS. Because no matter what reason someone has to create and run a virtual machine, there are things one should avoid at all cost, like a complete lack of security!
- Atlas OS
- Geolocation
- Tweetdeck
- Kick
- Identity Protection
Tip: Atlas OS
Last week I was going over some tweets by Daniel Card, aka mRr3b00t, about a new, stripped down Windows environment called 'Atlas OS'. Even Linus Tech Tips posted a video about this on their YouTube channel. I know for a fact that within the OSINT community there are people that use a slimmed down version of an OS for virtual machines, but I wanted to post a strong warning here. Don't simply download an OS, configuration script, or even a pre-built image if it is not downloaded from the website of the original maker of the OS. Yes, there are some pre-built environments that have been shared by me before, like Tsurugi, which can be called an exception. But in this case, Atlas OS removes all security features that makes Windows safe to use, like Windows Defender and security updates!
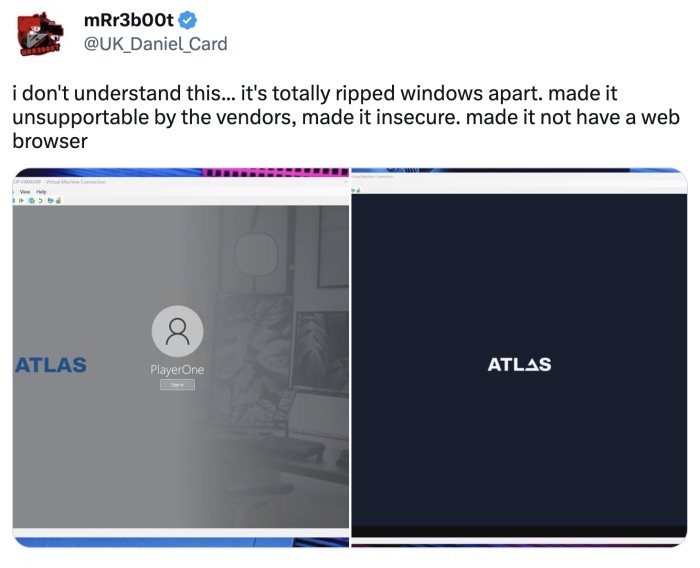
Do you want to investigate adversaries and visit all kinds of shady websites, without any form of protection? With the only plus side of sparing some seconds while clicking through some sites? The AtlasOS team has responded on Twitter that they will show a warning about disabling these featured in an upcoming release. Let me end this section with a general tip from me, and probably the rest of the InfoSec community:
better not do it at all!
Article: Geolocation
Steven 'Nixintel' Harris posted another geolocation tutorial earlier this month. He talks about a challenge that was posted by Conor Nolan on January this year. In the article he explains how he used small details in an image to generate enough clues to find the correct location. Again this shows the importance of going over the fine details of an image when being tasked to geolocate it, and Steven again takes us along his thought process when dealing with these tasks. Thanks again for the great explanation!
Link: https://nixintel.info/osint/...
Tutorial: Tweetdeck
Sofia Santos wrote an article on Tweetdeck, and has updated it to reflect the most recent changes. This post goes over how Tweetdeck is used to create columns with searches, profiles and lists to keep tabs on a specific topic. This is a wonderful tutorial for everyone that hasn't used Tweetdeck yet. And with Twitter slowly becoming an uncensored, unregulated, right-winged platform, the importance of monitoring this platform might be more important than ever. And while tweeting her updated blog post, she also shared a cheat sheet by Zilvinas Kucinskas, that lists all search operators for Twitter.
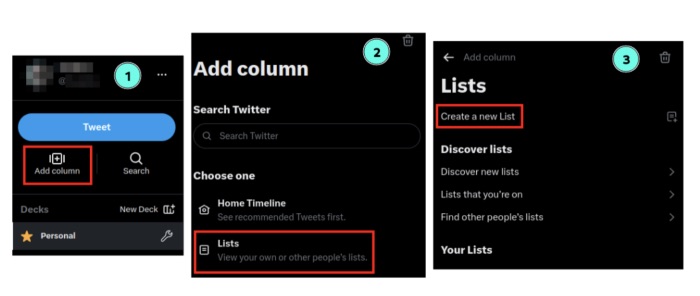
Tutorial: https://gralhix.com/2022/...
Cheat sheet: https://www.exportdata.io/blog/...
Tip: Kick
Kick is an alternative streaming platform, and I heard about it last week after it was mentioned by the OSINT community over at Kase Discord. And while checking the resources using the 'developer toolbar', I found some interesting URLs that can be queried without being logged in. Sadly enough, I haven't managed to get it working with cURL, since they seem to check whether JavaScript is running.
https://kick.com/api/v1/users/{username}
This API endpoint on a user, gives basic information on the username, which is also visible on the page itself. One extra thing that is mentioned is the numerical user ID, and a link to the profile image.
https://kick.com/api/v1/channels/{username}
The v1 of the channel endpoint, gives the most information. Most noteworthy are the following fields, that aren't visible by simply browsing there:
| Entity | Information |
|---|---|
| name_updated_at | Date and time when the channel name was changed |
| banner_image | URL of the banner that is used |
| user | It contains the field email_verified_at, with a date and time of email verification |
| chatroom | Information on when the chatroom was created and updated |
| previous_livestreams | Overview of the last live streams, including a dates and times of the stream, publication and the last update |
| verified | The channel ID, creation date and the last update of the verification status |
There is also a v2 of the API, that can be found at:
https://kick.com/api/v2/channels/{username}
It has mostly the same information as the v1 endpoint, but is a lot more slimmed down and lacks information on a few things, like the overview of previous streams.
There are more API endpoints, but most of the information can be seen in the browser itself. But if you do find more interesting information, do share them with the community!
Tutorial: Identity Protection
Earlier this month the 'Special Operations Command' of the US Army released their updated 'digital identity protection toolkit'. This extensive guide is full of tips and hints on how to protect your identity online. On their website you can download the full 160-page PDF-file, or you can download the general sections separately. They also have so-called 'smart cards', with information on the most common social media platforms, fitness apps, and other websites. This resource is an absolute must if you are looking to protect your online identity, or need to tighten your OpSec!

Link: https://www.soc.mil/IdM/publications/IdMpubs.html
Have a good week and have a good search!
