Week in OSINT #2022-47
This week I dive into tips and TryHackMe, Steam and scripting, and some other things from the world of OSINT!
Over the last few months all sorts of threat intel accounts on Twitter have been using the hashtag #OSINT. This, combined with all sorts of worldly turmoil and wars, it has been really tricky to find some interesting new content on there. But there are still tips and tricks out there, and this week, I gathered the following topics for you:
- TryGeolocateMe
- Steam OSINT
- Bash Scripting
- Practical OSINT
- Instagram Metadata
Tutorial: TryGeolocateMe
Early 2020 TryHackMe user Bee created a room called 'geolocatingimages'. I didn't see it before, but stumbled upon it recently. In this room you work your way through multiple levels of geolocation tasks, ranging from simple reverse image searches to finding IP cameras on Shodan. This is the same user that created the Shodan room, but this time it's about practising your geolocation skills.
Link: https://tryhackme.com/room/geolocatingimages
Tool: Steam OSINT
Over on the TOCP Discord, it was Forthe again who shared a new tool. This Python script enables you to get a better insight into a Steam user. It dumps the public friends list, but also gives a peek into interactions between users. By investigating these interactions, it can give you a better understanding of who might be a 'closer' online friend.
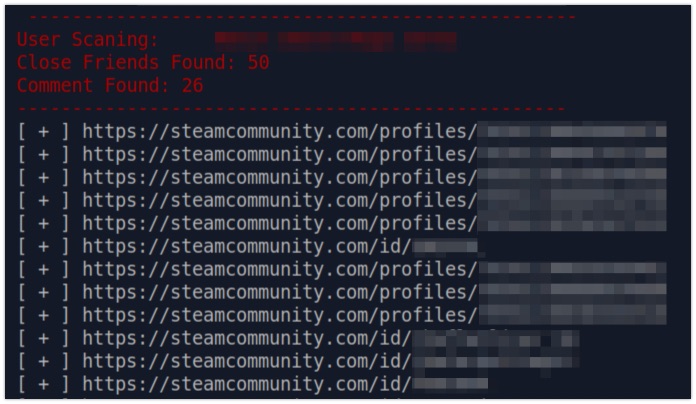
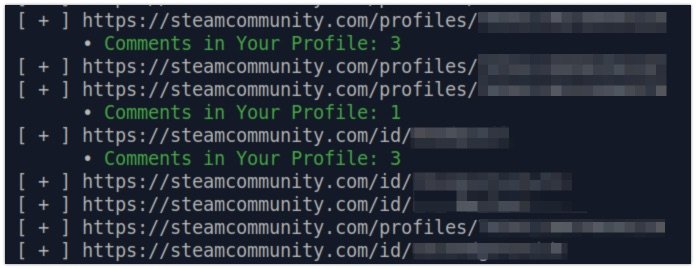
Link: https://github.com/matiash26/Steam-OSINT-TOOL
Media: Bash Scripting
OSINT Dojo made a short video on bash scripting, standard scripting language in Linux and MacOS. With this little tutorial you learn how to create a script that will run multiple user enumeration tools, and save all the information in a text file. These small scripts can not only speed up the information gathering process, but also makes sure you don't forget to run certain tools.
Link: https://youtu.be/hrXZv0hST0M
Media: Practical OSINT
Join Matt Ashburn and his guest Brian Fuller from Mercyhurst University, where he is director of operations for the Ridge College of Intelligence Studies and Applied Sciences. In this podcast Brian discusses hands-on tips from the field of OSINT. I wished this episode was a lot longer, but it still has some good tips on things like operational security. Learn some very basic things, like keeping an eye on different time zones, or making sure to visit other sites before and after visiting a specific target. Another great episode from NeedleStack by Authentic8!
Podcast: https://pod.link/1600516532/...
YouTube: https://youtu.be/RMzz_yB7DUs
Tip: Instagram Metadata
Until a few months ago, it was possible to retrieve the JSON data of an Instagram post by adding something in the URL. Then it stopped working, and there were some workarounds. But lately I've seen people post a new and slightly edited version of it, and this one works as a charm!
{IG URL}/?__a=1&__d=1
I suspect the addition of __d=1 is a parameter to tell Instagram that we are working with a 'desktop' version of Instagram. I don't have an older example at hand, but the amount of information that is sent back also seems to contain more than before.
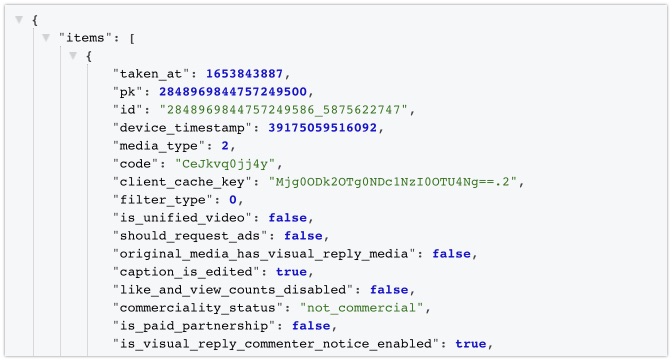
Have a good week and have a good search!
