Week in OSINT #2022-48
This week's episode contains some Mastodon, TikTok, GitHub and a personal tip on URLscan to find interesting websites.
Last week I had so much fun going through several articles, tools and tips that are featured in this episode. I loved playing around a bit more with TikTok, and has a blast with GitFive! There is so much information and knowledge out there, and I love learning from all of you. And last week I learned about:
- More on Mastodon
- TikTok's Privacy
- Investigating TikTok
- URLscan Resource Hashes
- GitFive
Tutorial: More on Mastodon
In the last few episodes I already wrote some tips and hints on how to investigate Mastodon. But now Nihad Hassan has written a lengthy guide on this platform. He starts by explaining its structure, how it works, and most importantly, why it is completely different from any other social media platform out there. He then touches on some investigative techniques that will help to shed some more light on how to navigate on this platform. I can't wait for part two of this great article!
Link: https://www.secjuice.com/mastodon...
Tip: TikTok's Privacy
Last month it was touching the headlines everywhere, but since I was a little busy I probably missed it. But TikTok has changed its privacy policy, to include statements that, among four other countries, China is able to access lots of information on European users. We all knew that this was probably happening anyway, but now it has been made public. This also left me thinking about operational security, more than ever before. Some general tips about operational security that I try to adhere to, might be useful in this case:
If possible, spoof your location
I have a phone that is not only rooted, but also spoofs its location by changing the GPS based location sent to the phone and its apps. This can also be achieved easily by using something like an Android emulator. You might stand out if using an emulator, but with enough random browsing around, you could still try and hide some high profile investigations.
Don't immediately visit your 'targets'
Whenever I open up a social media, to investigate a profile, I spend 5 to 15 minutes doing other things first. I like posts, reblog/repost them, add reactions, click on shared links et cetera. Then I quickly touch on some profiles, to get a first glance, but also look at other profiles, related or not.
Be active and unsuspicious
If you do have time, just open your app, like TikTok, and have a look around. I actually use my socks once in a while, simply to view some actual funny clips. It might be a bit of a hassle, since I actually need to turn on a phone that is usually stored away, but it is worth it.
I think it is important to remember that whatever platform you are using, there are always risks involved. Wherever the company is based, there is always the risk of being flagged for a specific behaviour. But sometimes, like in this particular case, it might be important to look at your threat lever and adjust your actions accordingly.
I also want to mention this article, by Natasha Lomas over on TechCrunch: https://techcrunch.com/2022/11/03/tiktok-privacy-policy-update-china/
Tutorial: Investigating TikTok
Again on SecJuice, user bravoTF117 has written an extensive tutorial on information that can be retrieved from TikTok accounts. This article shares lots of handy, and important information and reading is an absolute must. I learned that the difference between the information visible in the mobile app, and the web-based version, is larger than I expected! This article can be slightly technical for some, but it is important to at least know that these differences are out there.
Link: https://www.secjuice.com/tiktok...
Tip: URLscan Resource Hashes
One of the sites I always keep in mind when researching websites, is URLscan. This website is community driven, and contains scans and information on public facing websites. But the best thing of this all, is that there is a lot of information in there that enables you to find more interesting, or connecting, sites. In this tip I will explain the basics on how to search for SHA256 hashes of files. For this example, I looked at the website of Epoch Times, a right winged platform.
Open up URLscan.io and locate the 'Search' option in the top menu. In the search field, you type in the domain name you want to investigate. If there aren't any results, you can start your own scan from the home page. After finding hits on epochtimes.com, you open one of them and click on the 'HTTP' section, and filter on images. There we see a list of resources visible in the HTML source code, among it a logo with the filename logo_eet.svg.
From there, you open up its properties, by clicking on the little spying glass on the right. A screen like this should open up, giving you more information on the file itself:
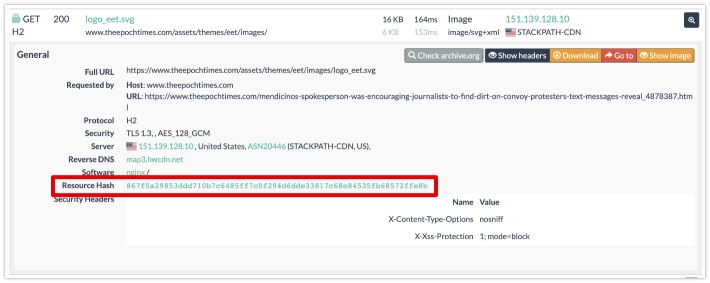
The SHA256 hash is actually clickable, so one simple click is all that is needed to query URLscan's database for this particular file. There are over 3000 hits, and I want to try and sift through some interesting, or unexplored, domain names. I chose to exclude domains that I was not interested in, and by adding these exclusions one by one, I created a small list of domains. These three domains were added in my search option, to be excluded from the results:
- theepochtimes.com
- epochtimes.com.ua
- lists.youmaker.com
To have a look at my exact search query, simply follow this link, or copy-paste the following search query yourself:
hash:867f5a29853ddd710b7c6485ff7c0f294d6dde33817c68e84535fb68572ffe8b AND NOT (page.domain:theepochtimes.com OR page.domain:epochtimes.com.ua OR page.domain:lists.youmaker.com)
It will present you with a small list of three domain names that were scanned quite some time ago, but might still be worth investigating if you are looking for content relating to the Epoch Times. This is just one way of using URLscan for open source investigations, and there is a lot more if you understand how to search their database.
Of course, this is just an example. Do check where and how the logo was used on that page, what the context is, and whether it is actually related.
Tool: GitFive
GitFive by mxrchreborn is a tool that digs up information from within GitHub profiles. It does need some initial setup, including a personal access token with certain rights, so this might not be for everyone. Besides that, it also needs the recent Python version 3.10, and the latest git (at least 2.28 or higher!). The script goes over a GitHub profile, looks at pull requests, creates repos and scrape commits, uses Google and Hunter.io for companies, and collects anything out there that gives information it finds. It returns a wealth of information, like names or aliases, email addresses, SSH keys and a lot more!
Link: https://github.com/mxrch/GitFive
Have a good week and have a good search!
