Week in OSINT #2021-12
Another episode filled with articles, tutorials, cheat sheets and some fun content in between. Whether you're into verification of social media, or need to dive into onion-servers, there's something in here for you!
So much awesome content is being shared the last few months. I wish I had a full day in the week to only read everything that is out there, but it's simply impossible. It seems to me that since the start of the pandemic more people started sharing information online, but also more free webinars and virtual cons the deal with open source intelligence. Talking about free, make sure to scroll to the bottom of this week's content for an interesting SANS stream later today!:
- Wistalk
- TryHackMe CTF
- IPFS Archive
- GeoGuessing with Deep Learning
- Toddington Cheat Sheets
- De-anonymizing Hidden Services
- Video Verification with InVid
- OSINT in Blue Teaming
Tool: Wistalk
Wikipedia is known for the extensive information that can be found on nearly any topic in the world, managed by the public. And when you have an open platform that is being maintained by that same public, it's possible that some weird things happen. In case you need to find out what a user did, there are several ways of doing that. You can find the edits of a certain page and go from there, and in case you have a username or IP address, these are some of the options.
Edits by user
https://en.wikipedia.org/wiki/Special:Contributions/{username}
Messages to/from user
https://en.wikipedia.org/wiki/Special:Contributions/{username}
Edits by IP address
https://en.wikipedia.org/wiki/Special:Contributions/{IP address}
Messages to/from IP address
https://en.wikipedia.org/wiki/User_talk:{IP address}
In case you need information on a specific user, and would like to download it, there's now a Python script that dumps all edits for you on your screen. Thank you for sharing this 7oaster!
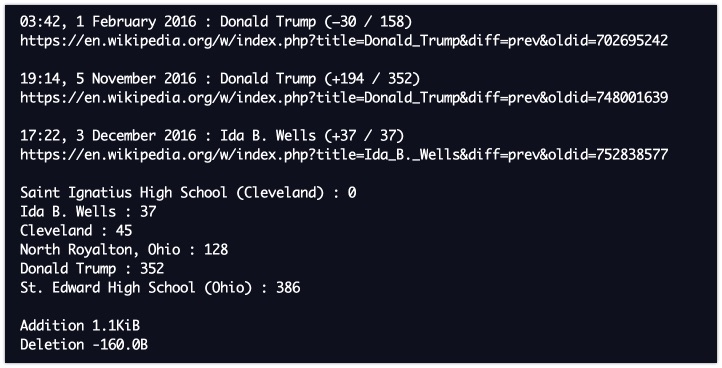
Link: https://github.com/altilunium/wistalk
Site: TryHackMe CTF
Jakob, also known as CoffeeOSINT, has created a new OSINT room on TryHackMe. This platform enables people to practice their cybersecurity skills by providing free challenges, ranging from lock picking to reverse engineering. Some of the challenges are accompanied by virtual machines, some only provide videos and there are also ones that let you dive into the world of OSINT, like this one.
Very pleased to announce the release of my new #OSINT room on @RealTryHackMe. I hope everyone enjoys it 😁https://t.co/KAFN9zjS21
— Jakob (@CoffeeOSINT) March 23, 2021
Link: https://tryhackme.com/room/somesint
Site: IPFS Archive

IPFS stands for the Interplanetary File System and is a decentralised peer-to-peer internet protocol used by several services and platforms already. Since IPFS makes it difficult for content to be taken down, it's a new way of circumventing censorship. Sites like https://d.tube/ are using IPFS for storage, and it even has extensions for all major browsers so you can browse content directly (link: https://docs.ipfs.io/install/ipfs-companion/). Besides that, it has some interesting archives, from the presidential daily briefs to a 5.4TB archive of the CCC. Thanks for sharing this Salaheldinaz.
Link: https://awesome.ipfs.io/datasets/
Article: GeoGuessing with Deep Learning
Andrew Healey has applied some science to the game of GeoGuessr. He has been training a machine to have a look around in Google Maps and after analysing the environment guess the possible location. Some very impressive results here, and I'm curious whether this could be applied on a bigger scale for law enforcement or OSINT4Good initiatives!

Link: https://healeycodes.com/geoguessing-with-deep-learning/
Tutorial: Toddington Cheat Sheets
Here's another link shared by 7oaster on Discord. The website of Toddington has a nice list of cheat sheets available for OSINT researchers. From investigative steps to browsers, and from Google searches to guidelines for law enforcement requests on the most popular social media platforms.
Link: https://www.toddington.com/resources/cheat-sheets/
Tutorial: De-anonymizing Hidden Services
Doctor Chaos has written an article about how to investigate onion sites and especially the servers they run on. It's a fact that some servers are configured in such a way that attribution, a server name or IP address is visible. The article can be slightly technical for some people, but in case you are slightly tech savvy, I recommend you to read this article. With it comes a huge flow chart with all the possible steps you could take! I might actually recreate it for myself in XMind or Diagrams (formerly known as Draw.io), to make it a bit easier to read and use. Because I never know when I need it.
I just published my first guide: https://t.co/zcDCoQZ5Ix
— Doctor Chaos (@ChaosD0c) March 27, 2021
Two high-level concepts and a flowchart that you can use to potentially deanonymize and locate hidden services. #OSINT
Link: https://chaos.institute/deanonymizing-hidden-services-guide/
Media: Video Verification with InVid
Nico 'Dutch OSINT Guy' Dekens has created a short video on the awesome tool called the 'InVID-WeVerify toolkit'. I've been using the tool since September 2018 when it was an online tool that was being tested. It has amazing capabilities for video and image verification and is targeted towards journalists to verify content that is shared on social media. Here he shows just some of the features that the software has.
Video: https://www.youtube.com/watch?v=UTyaEjVHL-w
Extension: https://www.invid-project.eu/tools-and-services/invid-verification-plugin/
Media: OSINT in Blue Teaming
Make sure to set your reminder his Monday, because at Monday 29th March at 12:00pm EDT (that is 16:00 UTC), there will be a live stream with Micah Hoffman, Nico Dekens, Ismael Valenzuela and Ryan Nicholson on how open source intelligence can be used in several disciplines. Join them online today and see what else is there besides social media to investigate!

Link: https://www.youtube.com/watch?v=C-FNuDGvBR0
Have a good week and have a good search!
