Week in OSINT #2020-41
This week an important warning, some nice maps, tips and other things I encountered during my daily scrolling through all my news feeds and social media.
This week it's another interesting episode, starting off with an important warning about extensions and add-ons. Who would have suspected that a well known browser extension would exfiltrate data, or maybe even act on your behalf? Working in IT security it of course had crossed my mind, but we still use such extensions and add-ons as OSINT professionals on a daily basis. So we are reminded again that we need to investigate the tools we use, to make sure we don't put our sock accounts at risk, or share sensitive information with a third party. Remember the story about Lampyre, where it wasn't totally clear who was behind it? I've got something cooking and more news about that in one of the upcoming newsletters! But first it's time to have a look at this week's overview:
- User-Agent Warning!
- Airforce Bases Google Maps
- Reddit RSS
- Epieos Tool
- Automated Threat Intel
- ASN
Tip: User-Agent Warning!
When it comes to tools, sites or extensions, I usually try them out myself. When I didn't have time to do so, I usually write that down in the item too. Because it's important to know whether a tool works, can be trusted and nothing weird is going on in the background. And then I read the following Reddit post this weekend, and it struck me: Even a simple extension can be dangerous to use! So please be careful out there, because it can happen that your information is being collected without your knowledge or, like in this case, your sock account is acting up without your knowledge!
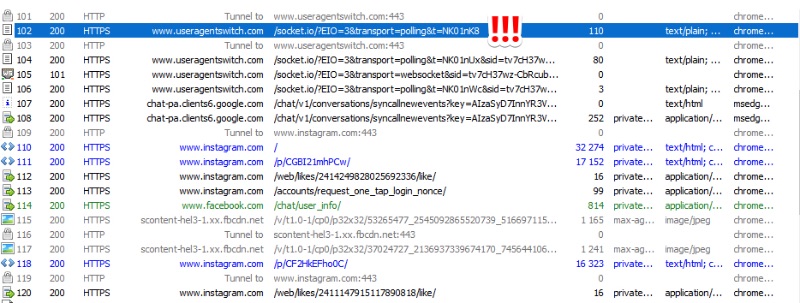
Link: https://www.reddit.com/r/cybersecurity/comments/j6gg2q/
Tip: Airforce Bases Google Maps
I've spent some time scraping Wikipedia and converting details of all publicly known Chinese airbases into a Google Maps format. I hope this is useful to #osint researchers. https://t.co/1EEGvRrICU pic.twitter.com/Wl36GzINX7
— Tom Jarvis (@TomTomjarvis) October 9, 2020
Last week Tom Jarvis came out with a Google map that showed the location of publicly known Chinese airbases. He also followed it with a tweet explaining what he did to generate the list, and it wasn't long before the great Gonzo replied with his own collection of pins. This time with a bunch of airbases from other countries. So if you are into this kind of information, I'd suggest you bookmark these public maps.
Chinese airbases: https://www.google.com/maps/d/u/0/viewer?mid=1dHrv7E_0mLVEzXdRxIGwaHBU16KEhrTj
Worldwide: https://www.google.com/maps/d/u/0/viewer?mid=1XmSGWNOcO2IwQnB-FFH4ueFPl6WIzKEC
Tip: Reddit RSS
Loránd Bodó gave out a free tip last week about Reddit. It's been known with a lot of people already for a long time, but in case you missed it or are new to the game, you can turn any subreddit into an RSS stream. The only thing you have to do is add the 'extension' .rss, add the link to your favourite RSS reader and you're good to go!
Quick #OSINT tip for those using @reddit.
— Loránd Bodó (@LorandBodo) October 9, 2020
Create an RSS feed to monitor a subreddit. Simply change the URL by removing the '/' and adding '.rss'
Example: https://t.co/j0yD5GWsiR pic.twitter.com/6RPBhnE2nD
Tweet: https://twitter.com/LorandBodo/status/1314548615071834112
Site: Epieos Tool
This tool has been out there since a few weeks, and it didn't even make my newsletter! Even though I use it myself at times for accounts I deem to be non-critical or sensitive. Why for that? I really don't know what happens in the back-end, or what is being stored in the access logs of the website. But this tool will give you complete links to the Google Maps reviews, a public calendar and public photo albums of any Google connected email account that exist.
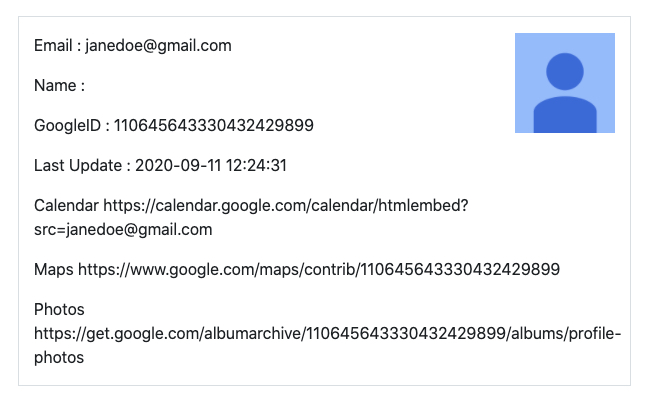
Link: https://tools.epieos.com/google-account.php
Tool: Automated Threat Intel
A totally unknown account to me is jmpshell, but they've recently started filling a GitHub repository with automated threat intelligence. A few suspicious apps, but also suspicious domains and active phishing campaigns are all added to the GitHub repo automatically every day. Star, share and use this!
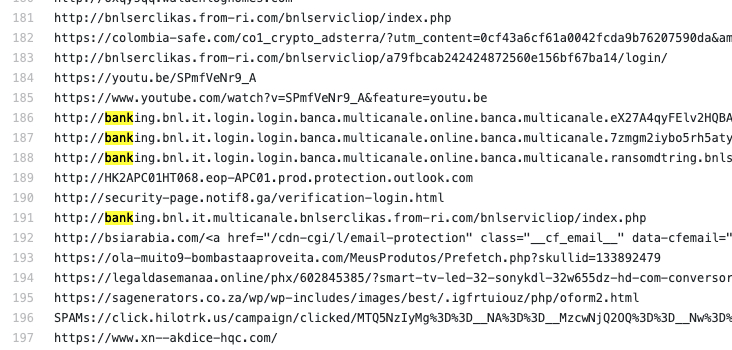
Link: https://github.com/jmpshell/ThreatFeeds
Tool: ASN
While visiting GitHub to have a look for new tools and scripts, I stumbled upon a really nice tool called 'ASN'. And the name already gives away what it's purpose is: Dive into ASN's, BGP info, IP addresses, domain names and organisations, and provide you with a nicely styled, deep analysis of the networks a specific IP or company is connected to. It uses freely available open API's to query for information, and a quick view at the code didn't reveal anything weird, so I'd suggest you try this one out yourself!
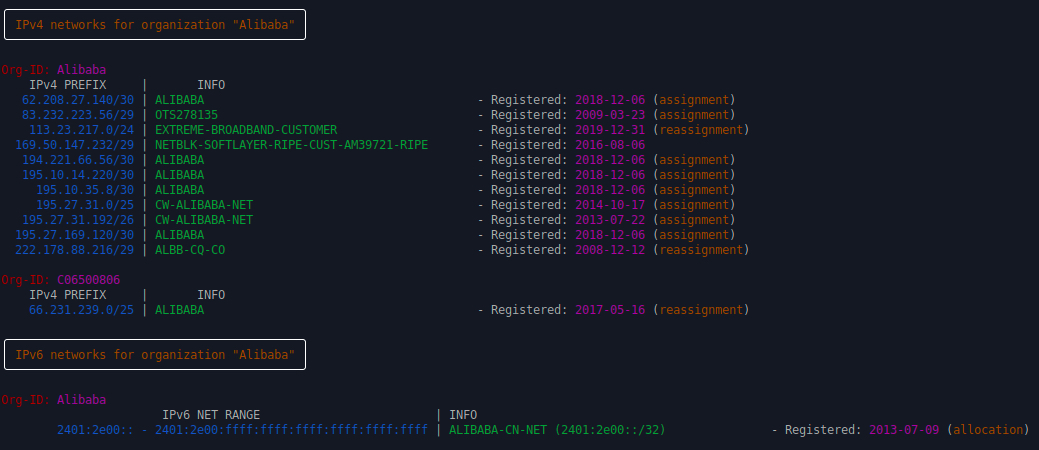
Link: https://github.com/nitefood/asn
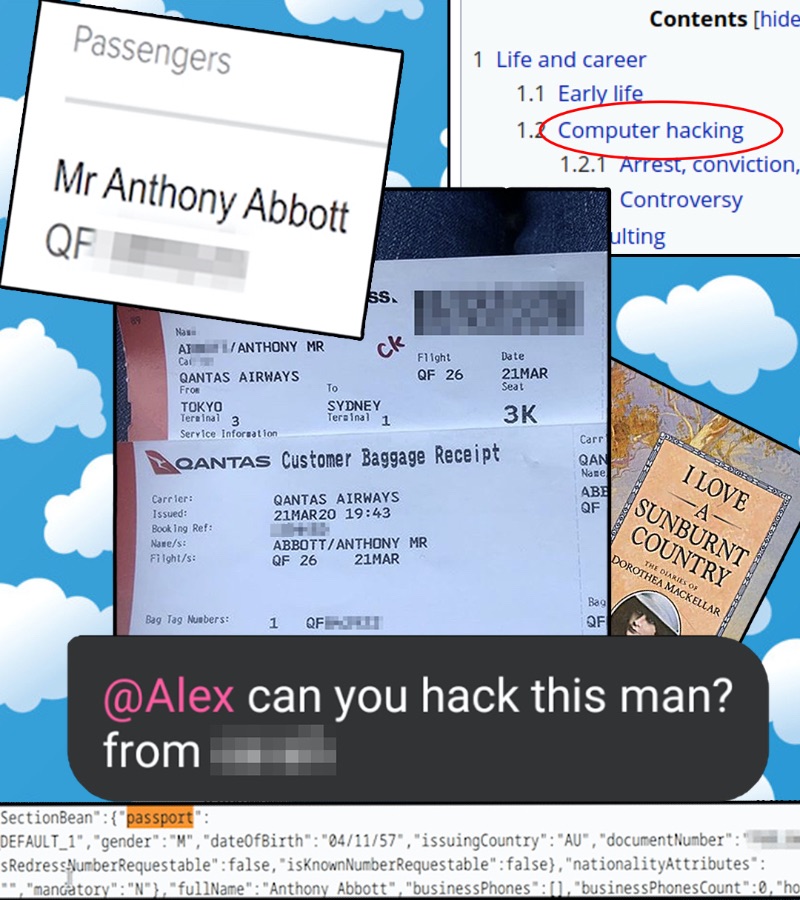
FUNINT: Aussie OSINT
A story about a boarding pass, a curious Aussie, and a really fun writing style!
Have a good week and have a good search!
