Week in OSINT #2019-49
The year is coming to an end, but my newsletters keep getting longer! Today a long list of articles, tools, interviews and investigations.
I tried to keep it short this week, but I simply couldn’t. I once stated before that after a few months I was afraid I was going to run out of links and tips, but things keep popping up! So thank you all for sharing, and thank you for tagging me with interesting resources lately. Here’s this weeks overview:
- Geolocating ꓘamerka Results
- Investigating Extensions
- StopChildAbuse Search
- Chasing Cars
- First Tweet
- Hiding in Plain Sight
- Interview with Mw-Osint
- Live News
- OSINT Projects
- UhOh365
Tip: Geolocating ꓘamerka Results
Wojciech is the maker of the tool ꓘamera, a nifty little tool that plots open devices like video and security cameras on a map. Besides another little update, Wojciech also gives some tips in this Twitter thread on how to find the exact location of the device, since Geo2IP isn’t that accurate.
Geolocating camera devices #osint #cybersecurity #ics #scada #shodan #shodansafari #geolocation
— Wojciech (@the_wojciech) December 1, 2019
[THREAD]
ꓘamerka supports new devices and screenshots! You can collect screenshots from open devices in specific location. I will show how to pinpoint device to precise place.
Besides the Python script ꓘamera, he also launched ꓘamera-GUI about a month ago. This is not just an update of his script, this is a totally separate version, that enables you to host your own GUI driven search tool based on it! Check it out on his GitHub page.
Link: https://github.com/woj-ciech/Kamerka-GUI
Tool: Investigating Extensions
Love to say thanks to @r3dhax0r for the https://t.co/9uy8F3EgdT tool!
— Micah (@WebBreacher) December 6, 2019
Dead simple to install and run and allows for the easy understanding of what your browser extensions can do.#osint #privacy #cyber pic.twitter.com/r20cFuE16Y
Twitter user r3dhax0r created a tool to investigate browser extensions by extracting all kinds of information like IP addresses, whois info, bitcoin addresses, Base64 encoded strings and email addresses. It can also upload the extension for scanning by VirusTotal, scan HTTP headers, view source code and what not. Awesome tool for investigators that want to check what their favourite extensions actually do in the background.
Link: https://github.com/Tuhinshubhra/ExtAnalysis
Article: StopChildAbuse Search
I have seen a lot of creative geolocation write-ups, I’ve seen people solve Quiztime tasks in awesome ways, but this is an example how it pays off to really pay attention to details in images! The article describes how investigators geolocated and chronolocated images that were posted via the Europol campaign ‘Stop Child Abuse — Trace an Object’.

The amount of work that went into this is staggering! Some topics that are covered in the article are:
- Plant taxonomy or dendrology
- Architecture
- Social media for reference material
- Historical weather information
Absolutely worth a read! And besides that, the Europol campaign is an awesome cause that can also use YOUR help! So please visit the link to the Europol website and help out of you haven’t done so. Do keep an eye out on the sub-Reddit (link) because a lot of images have been located already.
Europol: https://www.europol.europa.eu/stopchildabuse
Article: Chasing Cars
Mw-Osint is at it again with another great blog, this time about retrieving car information and images. He dives into VIN numbers, car detail sites, car spotters and has some good information and links in his blog. Feel the need to go after a car? Then do check out his blog. In general, his blog is one to follow anyway…
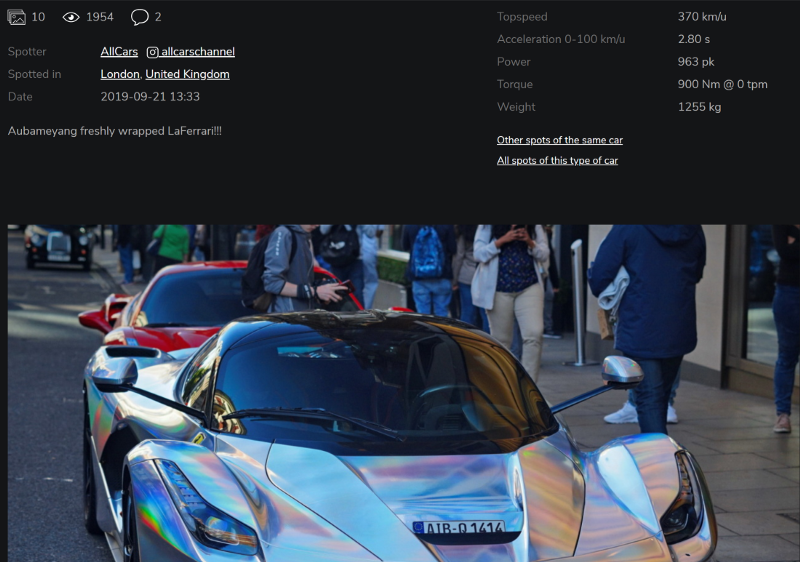
Link: https://keyfindings.blog/2019/12/07/car-spotting-and-osint/
Tip: First Tweet
Twitter user wongmjane created a bookmarklet that dives into a tweet and retrieves the original URL, quoted tweet or first person to tweet something. Thanks to Fiete Stegers for pointing this one out to me!
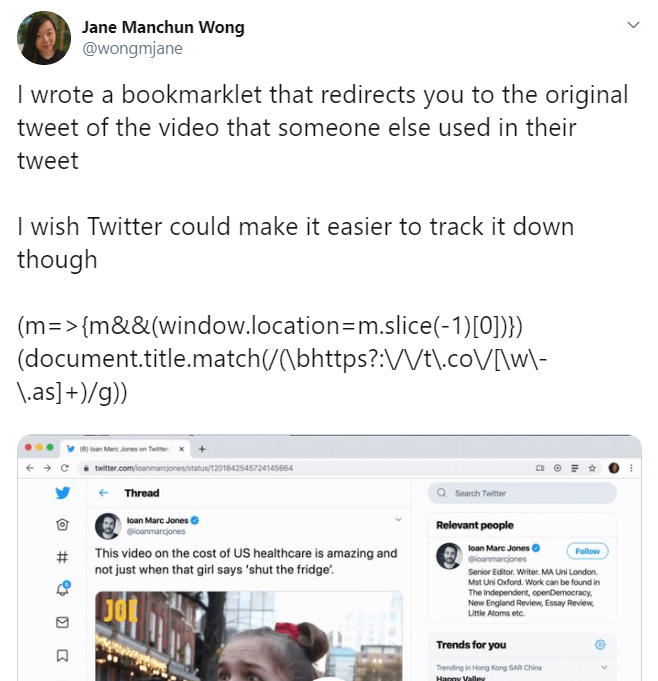
To save the bookmarklet, simply create a new bookmark with the following information inside the URL:
javascript: Javascript: (m=>{m&&(window.location=m.slice(-1)\[0\])})(document.title.match(/(\\bhttps?:\\/\\/t\\.co\\/\[\\w\\-\\.\]+)/g))or go to the tweet itself and copy the code snippet and use the site https://mrcoles.com/bookmarklet/ to create your own custom bookmarklet.
Tweet: https://twitter.com/wongmjane/status/1202293089395568640
Bookmarklet: https://mrcoles.com/bookmarklet/
Article: Hiding in Plain Sight
Twitter user Sancho Villa published an article last week that dives into some of the techniques used when dealing with tracking wanted persons. In part 1 of this investigation he is focusing on finding clones.
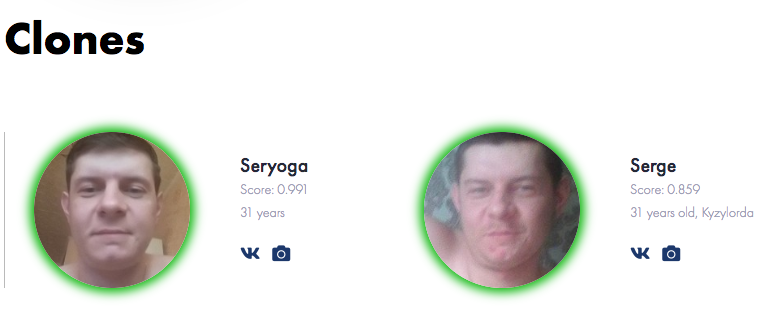
Link: https://medium.com/swlh/hiding-in-plain-sight-d3eec85a6956
Article: Interview with Mw-Osint
Last week I read the interview with Mw-Osint on the blog of osintme, where Matthias talks about his background, his experiences and his expertise. They also touch the subject of the Iron March dump and talk about investigating right winged extremists. Lately I’ve been reading some more articles on this blog and I have to say that there is some really great content on there! Of course there is the awesome interview with Nixintel, but also the article about some insight on Tor, his hardware and software setup articles and his article on Tor. So my advice: Do follow osintme on Twitter and keep an eye out for his next article!
Site: Live News
Are you looking into a specific geographical area and want to stay up to date with the local news? Maybe you are interested in the situation within Hong Kong or Syria, and couldn’t be bothered opening up dozens of web sites to track the latest news? Then Live UA Map is the site for you!
Tip: Click on “Select regions” on the top to find a specific area or country of interest that is not immediately available from the top menu.
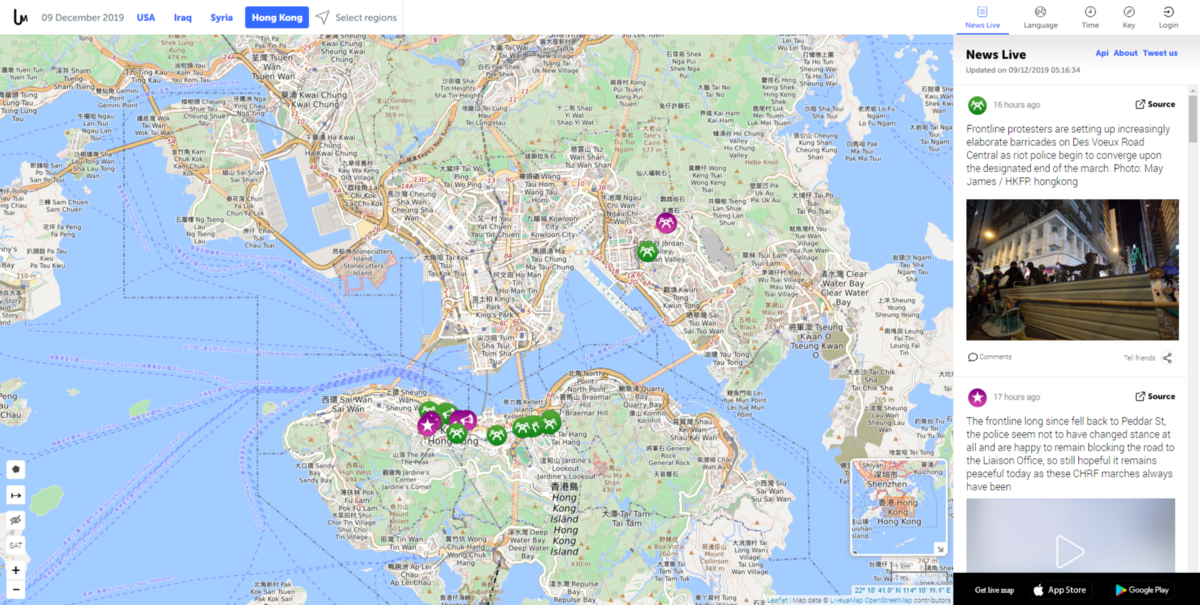
Link: https://liveuamap.com/
Links: OSINT Projects
Last week Salaheldinaz shared a great link in the OSINT.team chat. It’s a link list of OSINT projects directly from GitHub. And every link you open directs you to the readme of that particular GitHub page. The good part about this? It is all curated and indexed for you convenience, without having the need to search GitHub manually… And in case OSINT isn’t enough for you, there are topics ranging from Advertising to Web User Interface. So enough to check out!
Link: https://awesomeopensource.com/projects/osint
Tool: UhOh365
Another link from OSINT.team, this time from GONZO. This is a tool that uses the Microsoft Office365 API to check the validity of an email address. It’s simple, it’s gracious, it’s useful, it’s great!
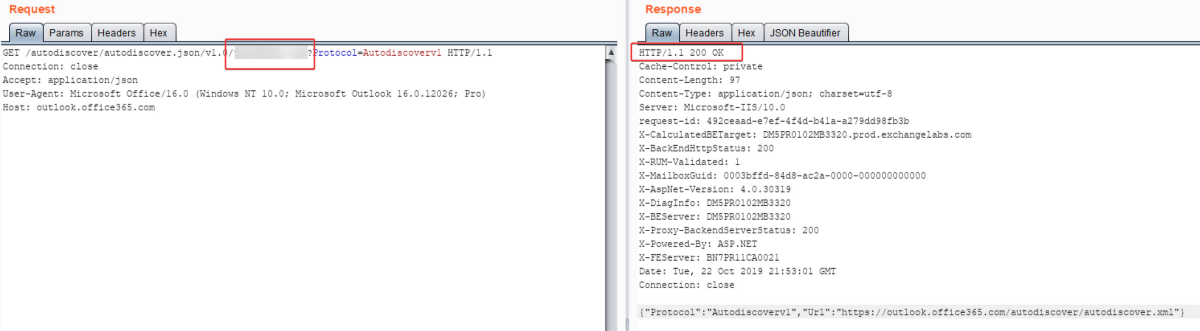
Link: https://github.com/Raikia/UhOh365
Have a good week and have a good search!
