Gathering Company Intel — The Agile Way!
Using a popular agile project management tool to gather intelligence on companies
Last week I notified a friend, who works at the public broadcasting service in the Netherlands, that their Jira board was exposed to the internet. Shortly after my notification the complete board was pulled offline, but it wasn’t until some time later that I realised what a huge treasure trove Jira actually is! In case you don’t know what Jira is, let’s just say it’s an expensive piece of software that replaces the sticky notes in the “to-do” corner of all the monitors in your department or company…
This article was written in September 2018. And even though the issues existed for many years and were reported to Atlassian by many people already, it may have taken this article to go viral for them to fix it. Because a few months after I publushed this article, most of the things in here were closed by default.
Jira is a tool that companies or agile teams can use to register their workflow. Another tool that can be used to do similar things (if we only look at the Kanban-style board) is Trello. If you don’t know Trello, then at least run a Google query to find some public ones to play with and be shocked about what people leave there to be found. This is the only screenshot in this article that I didn’t censor, since it is just too easy to replicate this query and this has been known for years already.
Jira is different though, and usually doesn’t give us an insight in the contents of the cards. But that does not mean there is nothing to find in Jira. On the contrary! I have played a lot with the Jira REST API endpoints before, which sometimes hold some golden nuggets when it comes to running projects or sensitive company data. But it was only after going over my notes and testing a few endpoints on public servers, that I realised that this is actually a perfect tool for recon on a company! So let me take you into the world of Jira and we’ll go over some endpoints where I will give some examples on the data that is retrieved and how the information could possibly be used.
One extra note before I continue though. During my research I found that directly querying an endpoint didn’t always work if this was the first connection to the server. But one simple visit to the Jira login page gave me a preliminary session token or cookie that seemed to be enough to give me the right to query. So if you find yourself stuck with empty results, go grab yourself a cookie!
Retrieving usernames
The user search endpoint is able to retrieve the best information out there, namely:
- Usernames
- Key’s (internal username)
- Account id’s
- Display names
And with a bit of luck, you could even retrieve email addresses or LDAP account names via such queries, depending on how the organisation has set up their Jira platform.
Thank goodness the amount of companies that had this endpoint open for unauthenticated access are few, but there actually are companies out there that have specifically set this option. If you find yourself lucky to find it during an assessment, you can query it as follows:
https://www.website.com/jira/rest/api/2/user/search?username=.&maxResults=1000This will retrieve the first 1000 users in the environment in JSON format. If there are more than 1000 users, then one can query on username=a followed by a new query on b and so on. An example of an actual result that is still open on the internet can be seen here:
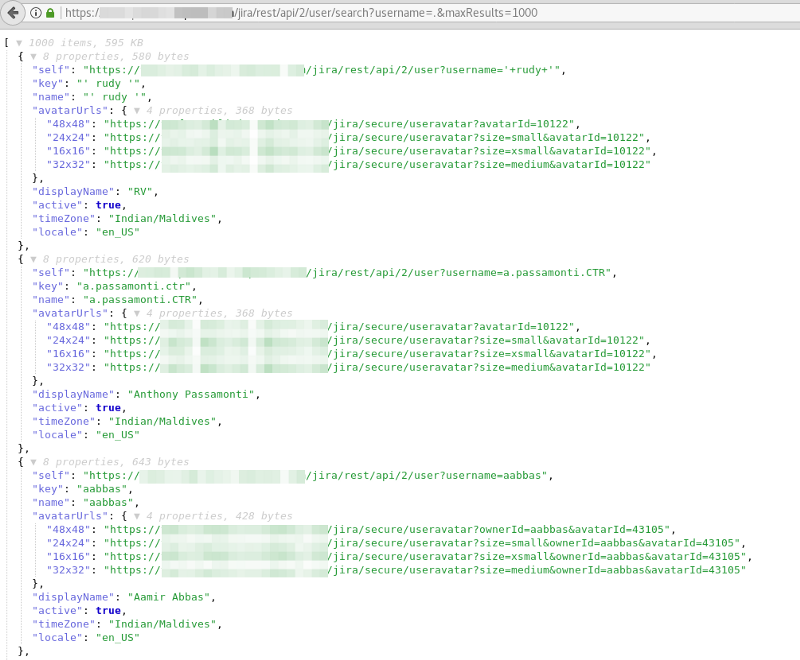
This data is of extremely valuable when it comes to social engineering or maybe even phishing runs that are used during an assessment. And during a redteam or pentest engagement possible usernames are of course something you love to find.
Listing projects
When the user search turns up empty, not all is lost. Because there is a lot more information to gather. Another endpoint to look at is projectCategory. This retrieves the first 1000 names and descriptions of projects that are registered in Jira. The query for this is:
https://www.website.com/jira/rest/api/2/projectCategory?maxResults=1000And the result of such query looks like this:
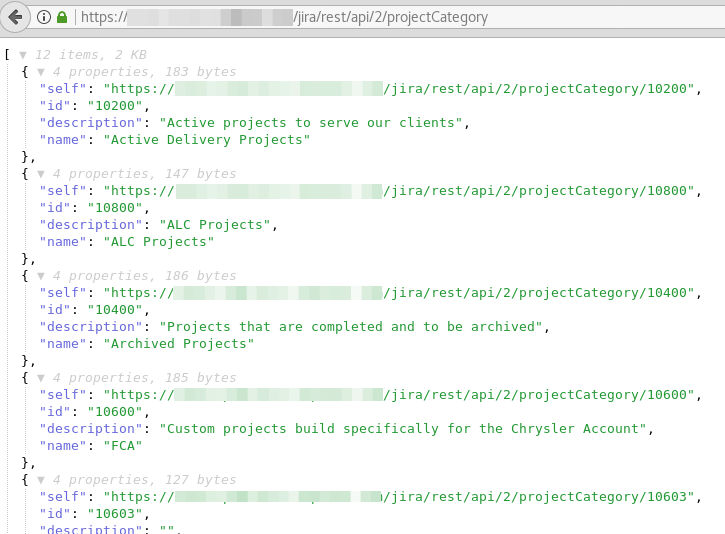
This is again information that is perfect for social engineering. But this can also be used to find possible partners or subcontractors, to gain more insight in their operations.
Finding Dashboards
When a project is handled by a specific team, or is big enough to have it’s own place in Jira, it is possible to create a separate dashboard for it. And these dashboards can also be retrieved via the API. The query to run is:
https://www.website.com/jira/rest/api/2/dashboard?maxResults=1000It retrieves the list of dashboards that are configured, with the names — usually a small description of the project itself — and a URL to the dashboard view, as can be seen here:
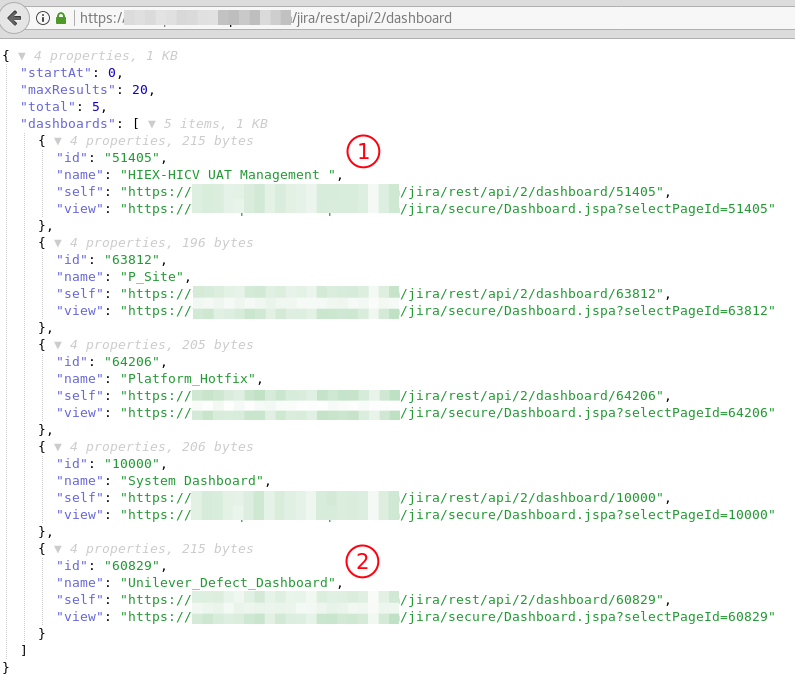
In the above screenshot we can see a dashboard that might be about “Holiday Inn Express” and “Holiday Inn Club Vacations” and on the bottom we see a “Unilever Defects” dashboard. Visiting the dashboards itself via the link that is visible under the name view may give away even more information, since they sometimes are configured to be viewable for non authorised users, or they contain some extra information via for instance a plug-in.
Gathering Other Information
Even though the projects and dashboards give the best results when querying — since they usually can be used without authentication — there might still be a need to get more information.
One endpoint to have a look at is the endpoint called groups/picker, that retrieves all the groups that are created. The query is:
https://www.website.com/jira/rest/api/2/groups/picker?name=.&maxResults=1000This retrieves the list of groups up to 1000 items. If we remove everything from the question mark on only the top 20 are retrieved, so I added some extra parameters to get the maximum amount of 1000 items returned for us. Pay extra attention to group names that include client names, project names or other descriptions that are slightly out of the ordinary.
After all this information is gathered there is one more endpoint to visit. Because another place to look for information are the default resolution texts. Just simple ask the Jira REST API for some information on that with the following queries:
https://www.website.com/jira/rest/api/2/resolution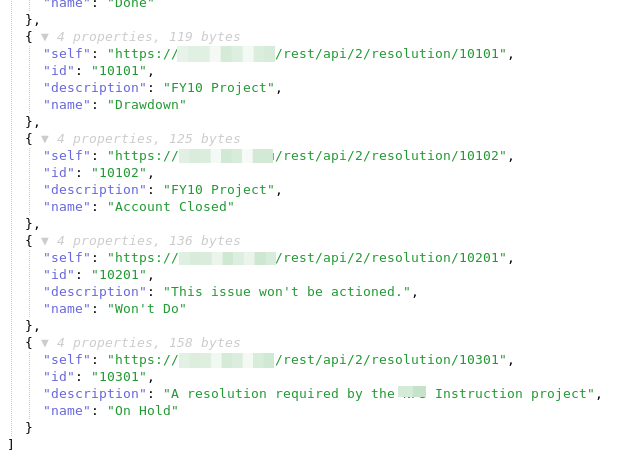
The resolution endpoint lists all of the available resolution texts that are configured in Jira. These are the default ones and the ones the editoris in that environment created extra. In the example above we for instance see a reference to a “FY10 Project”, whatever that may be. So even in those seemingly harmless resolutions there could be a hint towards something that is worthy of being noted.
Finding Jira
Finding Jira is as easy as Googling, as you expect. A simple Google query gives you thousands of dashboards on the internet, so there is a big change there is some information to gather. Just search for websites with “System Dashboard” in the title, that have the text “Atlassian” in the page and make sure to exclude the Atlassian sites themselves:
intitle:"system dashboard" intext:atlassian -inurl:atlassian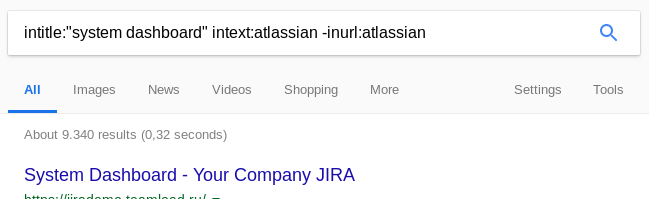
If a Jira dashboard isn’t indexed by Google, there is also our trusty Shodan or Censys that one can ask to retrieve all web servers that serve a website where the title contains the words “system dashboard”:
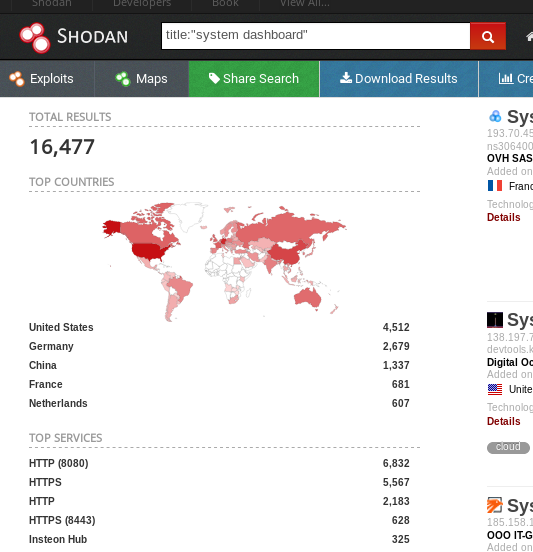
It is possible to narrow down the options by using a different query, for instance:
title:"system dashboard" html:jiraBut this still gives us almost 14,000 “System Dashboards” where the term “Jira” shows up somewhere in the website. And with “agile” and “scrum” being the buzzwords of the last couple of years, chances are fairly big that a company you are investigating has its own Jira instance running. And hopefully it is connected to the big bad internet.
Conclusion
There has been written a lot about Trello, where people simply forget to make a board with sensitive information private. Jira might be closed of for outsiders by default, but simply visiting the login page of any Jira System Dashboard gives a visitor a cookie that opens up a world of information. And this kind of information can be used for good — as I am discussing here — but could of course also have negative sides.
Do you really want to give people the opportunity to find out what secret projects your company is working on? And did you realise you shared the newly created dashboard for that sensitive financial information? Was it on purpose that you gave that silent partner its own user group? Realise your Jira board is connected to the internet, a tool that is used for mostly internal processes. It is there for everyone to see, to scrape and to (ab)use. But as someone who loves to conduct open source investigations, you won’t hear me complain about that…
