Week in OSINT #2020-37
Lots of links, tools and articles this week and it ain't even Christmas yet! From stories to Shodan and Tafferugli to Transforms, whether it's IoT or social media, you'll enjoy this weekly episode!
This week I've been taking my time collecting some interesting tools, tips and articles, but also revisiting some of my older blogs to update the link section on this website. As a result a few dozen sites have been added, and I'm close to reaching 230 links. As stated in the link section: It'll never be the most complete links collection ever, but what I do aim to do is to share links that:
- are grouped together for convenience
- cover as many topics as possible
- that I've used and gave solid results
- are free forever or have a free tier
- may be extremely niche
By providing a way to filter on tags, description or any of the URL, I also try to make it slightly easier to find a specific link. And to be honest, I've caught myself actually searching for a link myself already after I forgot a URL, so I know that at least one person is using it! Anyway, enough chitchat, it's time for this week's overview:
- Shodan Improvements
- Tafferugli
- OSINT IRL Stories
- Facebook Group Members
- CSE Maltego Transform
- Darkshot
- Exploring TraceLabs Submissions
Article: Shodan Improvements
Shodan keeps improving and enhancing their search engine, and that is the focus of a blog post that was published last week. Besides improving the performance of the search engine they also added som new features, like numeric ranges so you can now search for things like port ranges. And a second enhancement makes it possible to search within IPv6 network ranges.
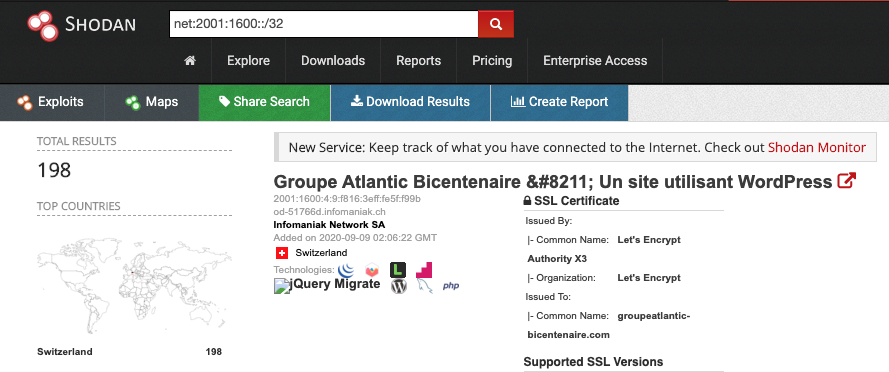
Link: https://blog.shodan.io/search-engine-improvements/
Tool: Tafferugli
Twitter user s0wdust has been very busy lately building a Twitter analysis framework. This web application is able to filter, collect and analyse tweets, according to his GitHub. It can show analytics and connections between tweets, users, hashtags and more, all from within a simple web application. I've played with the demo a little bit, but I know that by the end of this week I'll be running that in a VM for a solid test drive, because it looks awesome!
GitHub: https://github.com/sowdust/tafferugli
Demo: https://www.tafferugli.io/
Article: OSINT IRL Stories
Twitter user Hatless1der started collecting some real life examples of how OSINT was used to investigate an event. And I'm thrilled that me and MW-OSINT were mentioned with the article about unraveling the Norton Scam, amidst of other awesome articles by Benjamin Strick, Brian Krebs and the Citizen Evidence Lab of Amnesty International.
Link: https://hatless1der.com/osint-irl/
Tip: Facebook Group Members
When it comes to Facebook, there are few people that have researched the ins and outs of the GUI. And the only one I personally know of, is Technisette. She keeps finding new and interesting things like the differences between te old and new layout, and she now found out it is possible to see some historical events of a user within a group!
Pretty cool; click on a member of a Facebook Group to see their Group profile; see when they became a member, any group posts, recent posted photos and/or recent activity. #facebook #osint #osintcurious pic.twitter.com/rzBcoOaWg3
— technisette (@technisette) September 11, 2020
Tweet: https://twitter.com/technisette/status/1304338944843223041
Tool: CSE Maltego Transform
Well over a year ago Francesco Poldi created a Telegram CSE and last week he announced it was turned into a free remote transform for Maltego! For good measure he added the WeVerify CSE too, so now you can search within Maltego on a whole bunch of social media platforms. Simply add the transform seed to the transform hub, give it a name and description and off you go!
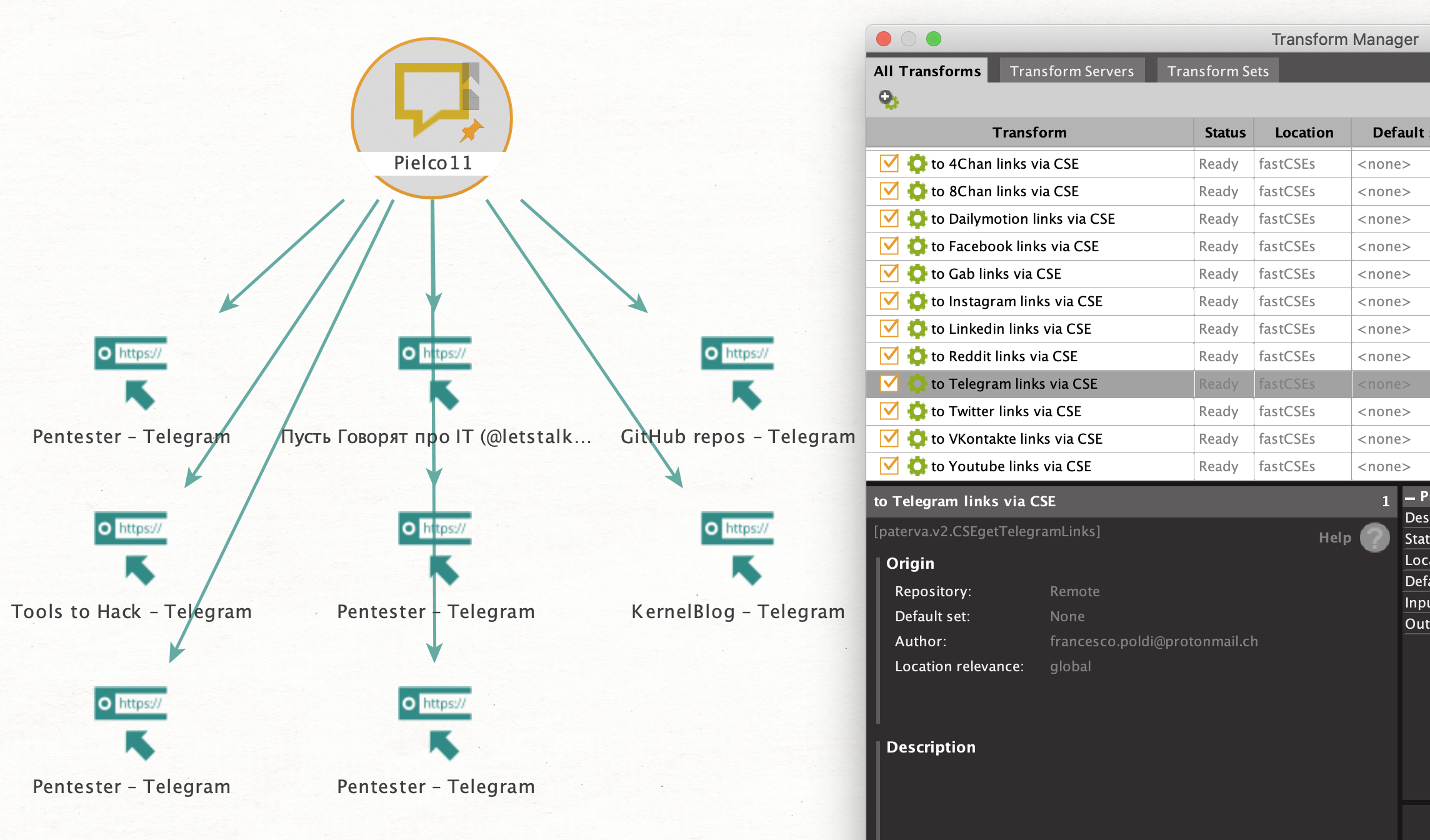
Link: https://cetas.paterva.com/TDS/runner/showseed/fastCSEs
Tool: Darkshot
Gonzo pointed out an awesome new tool, called 'Darkshot' that pulls all the publicly available Lightshot screenshots and uses OCR to grab sensitive information from them. You don't know why it is possible to do this? Well, just browse around a bit, because this has been known for quite some time already. It's even shown in the tutorials of Lightshot how to automatically upload a screenshot to the internet for immediate sharing. Another fairly new tool that pretty much does the same, is Shotlooter by 'utkusen' and which is even mentioned in the readme.

Darkshot: https://github.com/mxrch/darkshot
Shotlooter: https://github.com/utkusen/shotlooter
Article: Exploring TraceLabs Submissions
Twitter user AccessOSINT received some data from TraceLabs on the URL's that were used in submissions by contestants. He dove into these links to find out what kind of information they are able to provide and shares some of the most interesting links in this article. A really great blog for people that like to participate in these CTF's, but maybe also for other investigators that are looking for that one special link…
Link: https://accessosint.com/trace-labs-ctf-exploring-interesting-url-submissions/
Have a good week and have a good search!
