Week in OSINT #2020-03
A short update on the weekly OSINT landscape, from OpSec fails to open source data for journalists.
Hello all! Last week was quite an update, but after that life and work happened again, so time to keep it a bit more simple. Here are some really nice topics I’ve encountered last week:
- OpSec and Corporal Punishment
- Windows VM’s
- Introduction into OSINT
- Mitaka
- BIRD
Article: OpSec and Corporal Punishment
This article shows how important operations security is nowadays. Every footprint you leave online might be traced and bite you in your well camouflaged butt. This story had a somewhat happy ending, since it happened during a training, but still a good story to share!
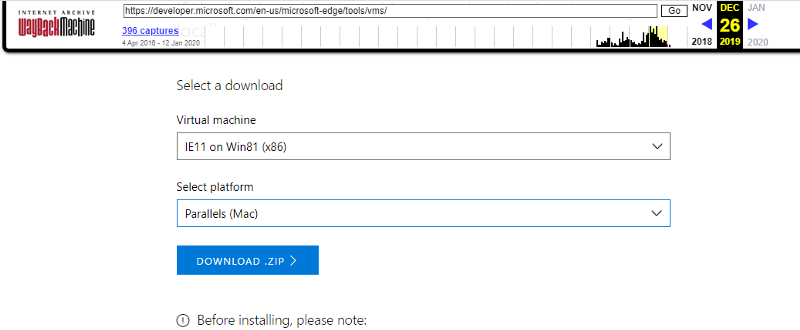
Tip: Windows VM’s
Most of the Windows test images that were available for download have been removed by Microsoft from their website, besides Win10. But thankfully Twitter user olihough86 found the download page has been archived for our convenience, but the images are still out there. So if you still need a Win7 or Win8.1 image for Virtualbox, HyperV or any other flavour, then quickly go to the internet archive, choose your download and go to the (still) active link. Thanks for the tip!
Media: Introduction into OSINT
WebBreacher and OSINTtechniques had a chance to meet and made an awesome beginners tutorial! The result is an introduction into OSINT that covers finding usernames, email addresses, phone numbers, google search operators and saving your data. And this might be useful for first time participants on the upcoming global CTF too!
Link: https://www.youtube.com/watch?v=PNeCqw8OLeA
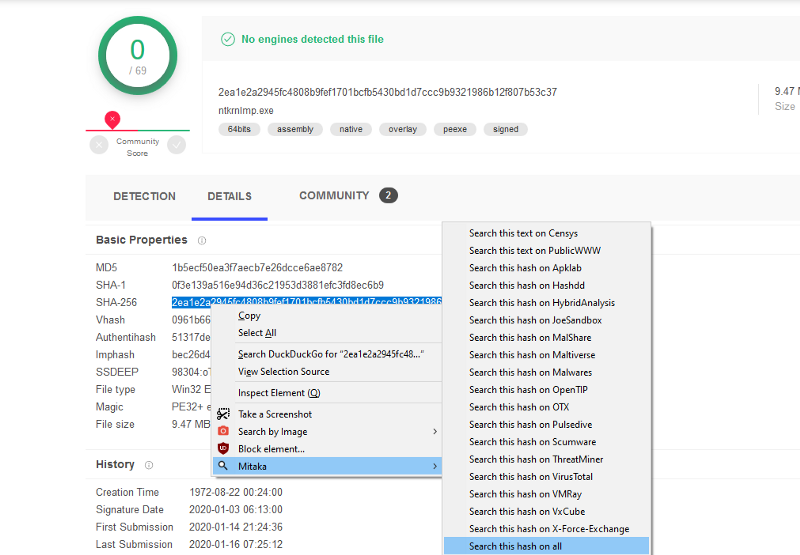
Tool: Mitaka
The tool Mitaka was featured in 2018–35 and in 2019–41, but has seen a lot of updates since so it was time to feature it once more. This open source tool (source code is here) gives you a right-click menu that enables you to search for text, BTC, IP addresses, email addresses, URL’s, known hash formats and a bunch of other things! While the new Chrome extension isn’t released yet, the Firefox add-on has been updated already with all the new features, like the ‘search on all’ function.
Chrome: https://chrome.google.com/webstore/detail/mitaka/bfjbejmeoibbdpfdbmbacmefcbannnbg
Firefox: https://addons.mozilla.org/en-US/firefox/addon/mitaka/
Site: BIRD
Twitter user Friedrich Lindenberg shared a nice the other day. It is a link to the BIRN Initiative Resource Desk, or BIRD in short. It has a bunch of tutorials, videos, tools and open databases on their website and they position themselves as an interactive platform for journalists.
Link: https://bird.tools/
FUNINT: Stalking
Thanks ex16x41 for the clarification!

Have a good week and have a good search!
