Week in OSINT #2020-04
Another week, another collection of links, tools and articles from the world of OSINT!
Welcome to yet another episode of this weekly newsletter. This week we look at all kinds of weird things, like: OMG’s, LA, APT’s, Pokémon and samurai. Got your attention? Let’s go!
- Outlaw Motorcycle Gangs
- Camopedia
- Tsurugi
- OSINT in Threat Intelligence
- TikTokOSINT
- LA Open Data
- Telegram Scraper
- Pokémon GOSINT
- WordPress IP Leak
Links: Outlaw Motorcycle Gangs
Twitter user CassiusXIII wrote an article about identifying outlaw motorcycle gangs via their patches and logos. It contains Lots of links to other web sites about gangs that were identified in Australia or New Zealand.

Link: https://medium.com/@CassiusXIII/identifying-outlaw-motorcycle-omcg-gang-symbols-590a1245ca1d
Site: Camopedia
OSINTtechniques shared the URL of Camopedia last week. This web site is probably the biggest resource when it comes to camouflage patterns from all over the world. It has been a great source during previous investigations I’ve participated in, and I know a lot of journalists and investigators are familiar with the site too. I didn’t realise I never shared it before, so thanks for the tip!

Link: https://camopedia.org/
Article: Tsurugi
InquisitorH3x wrote an article about how to configure and install a Tsurugi VM. This Linux distribution has been featured before in episode 2019–08 and it is just another big toolbox for OSINT enthusiasts. Read my older Week in OSINT for an in-depth review and jump to Inquisitor’s blog to read how to configure and install it in VirtualBox.
Link: https://medium.com/@inquisitorh3x/tsurugi-setting-up-your-environment-9e3a9225f380
Article: OSINT in Threat Intelligence
Sophos published an article about how OSINT is used within threat intelligence and in their article they have some nice hints and tips about public resources on the topic. From lists of APT’s, the techniques they commonly use and several links to public resources.
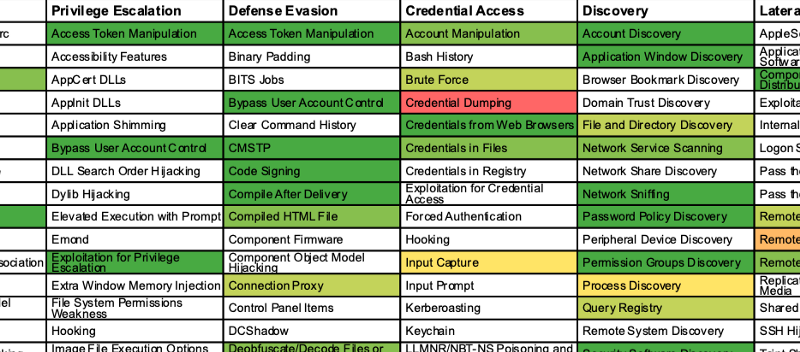
Link: https://news.sophos.com/en-us/2020/01/15/compiling-open-source-threat-intelligence-for-threat-hunts/
Tool: TikTokOSINT
TikTok is becoming more and more interesting for OSINT-ers out there, and that means that tools that gather basic info are also being written for it. This tool dumps all kinds of public data on any given user in a nice and easy to use format. Thanks harrywald80 for the tip!
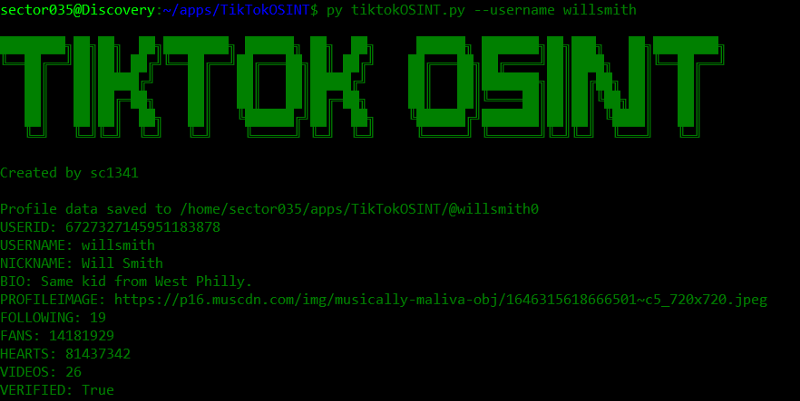
Link: https://github.com/sc1341/TikTokOSINT
Site: LA Open Data
Twitter user KodyKinzie wrote a Python script to search the public records of LA from the command line. You can search for a restaurant or cafe, find the owner, address, their violations and other public information provided by the city of Los Angeles.
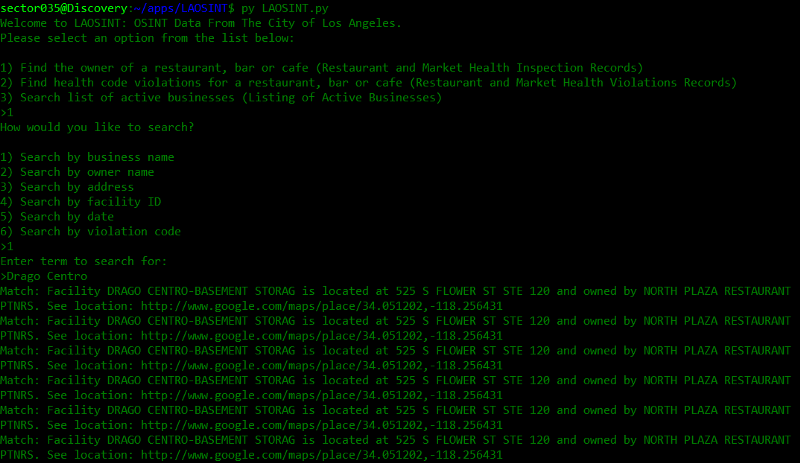
GitHub: https://github.com/skickar/LAOSINT/
Link: https://data.lacounty.gov/
Tool: Telegram Scraper
When I went over some material for this newsletter, I noticed that ex16x41 had sent out a tweet again, about an Telegram scraper! I didn’t have time to download and install it myself yet, but I’ll surely have a look as soon as I have time to do so. So for all you data gathering infoholics, time to party!
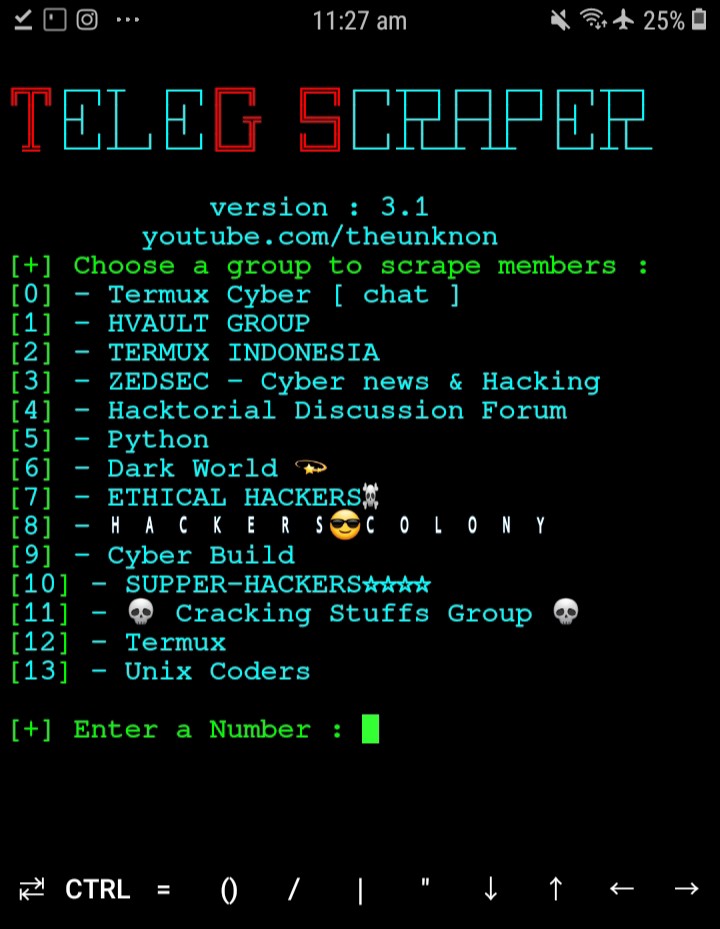
Link: https://github.com/th3unkn0n/TeleGram-Scraper
Article: Pokémon GOSINT
Twitter user sinwindie wrote an article on OSINT within Pokémon Go and just published a second one. It goes over all kinds of pieces of information one can gather on accounts, people, locations et cetera. Time to grab that smartphone and start heading to your nearest gym!
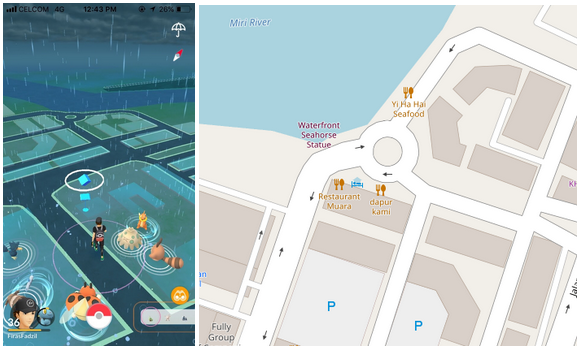
Part I: https://www.secjuice.com/pokemon-go-osint-techniques/
Part II: https://www.secjuice.com/part-2-pokemon-osint-techniques/
Article: WordPress IP Leak
Cloudflare is known to protect websites against attacks and provide some form of anonymity when it comes to hiding your IP address. But now Twitter user djnemec has found an innovative way to uncover the actual IP address of a web server running WordPress: Via the pingback option that most WordPress sites have enabled by default!
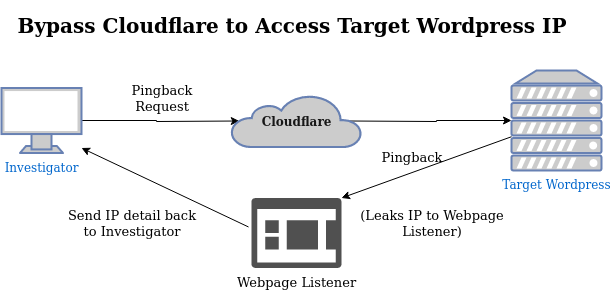
Link: https://blog.nem.ec/2020/01/22/discover-cloudflare-wordpress-ip/
Have a good week and have a good search!
