Week in OSINT #2018-20
Just before my last Medium post went online earlier this week, I suddenly thought back about all the newly launched websites or updated tools that have been reaching my eyes year after year. And despite the fact I will never use each and every OSINT tool that is out there, it would still be a waste if I didn’t take some time and create a little post about a few of these at the end of a week.
So here is the first edition of hopefully many more to come, provided I have enough time or something weird happens. Some interesting articles, tools or websites that deal with OSINT from last week (okay, and a few older ones since this is the first edition)
Website: GPSies (now AllTrails)
Something that really gained momentum this week was the site of GPSies and especially the track search. We all remember the buzz about the Strava heatmaps that showed military bases all over the world? Well, at GPSies they have loads more information and they even provide a nice search tool for it too! They also have several different maps to choose from and even things like a layer to show waymarked hiking or cycling trails.
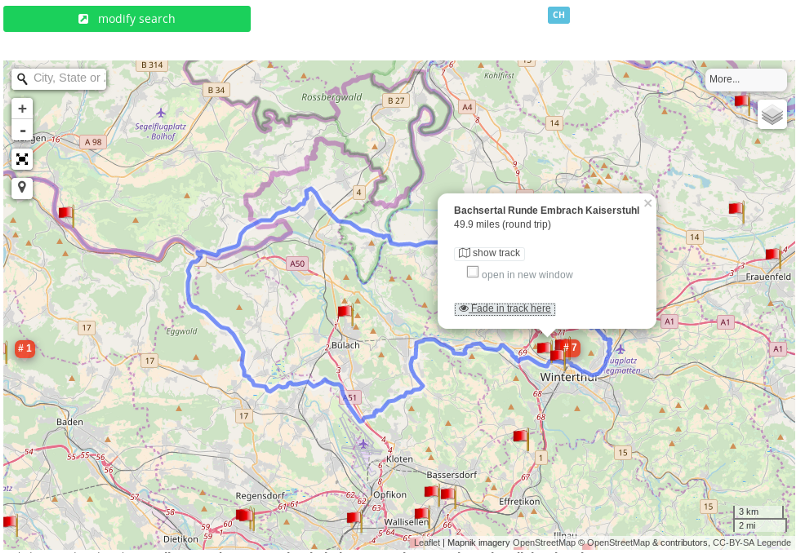
You can do advanced searches on parameters like the type of track or its length, but it is also possible to search for specific usernames. One thing to remember when searching for those, it automatically gives back the results where the provided name is a partial match of one in the database. So if you search for “Karl”, you will also get the results of the username "karlis" for instance, no need for wildcards!
A great tool (not just for the hiking fans) and again, one extra database to have a look at when you try to find someone on the internet.
Link: https://www.gpsies.com/trackList.do
Tool: Goohak
Goohak has had an update last week and even though this tool is more targeted towards hackers and pentesters, it might actually be beneficial for researchers too. It is a simple bash script (for Windows users: This can easily be re-written) that you can clone from their GitHub repo. After that, simply change the name of your default browser (Iceweasel, Firefox, Chromium, etc) and run it against a domain name you want to investigate. Right after pressing enter, it fires up a new browser instance and opens a whole bunch op tabs in rapid succession.
Each of these tabs will have a different website containing different information. From certificates and the corresponding domain names, results of Google dorks looking for common documents or employees, Whois information of the domain, and even the search results of possible company information on Pastebin. The script is extremely simple, and even though there is a lot that could still be added (like more pastes!), it is a very nice and simple tool that could be used as a first step in online investigations towards companies with an online presence.
Link: https://github.com/1N3/Goohak
Tool: Twint (archived)
If you feel the need to do some serious Twitter research, and you need a bunch of tweets, then you might want to have a look at Twint! No need to login (for public tweets), and also no API needed, since it will scrape Twitter to retrieve all Tweets of a user (maybe use a VPN connection for this, just to be sure).
And besides that, Twint has a great list of options that you can use! You can search within time frames, search within a geographic radius, search for keywords, scrape followers or followed accounts and a few more options. Regarding output, you have a few options, from a text file or CSV, to the option to send it to Elastic, in case you need to do some serious investigation on the data. A tool for the more serious investigator, but one that should be checked out, as long as you run some form of Linux distro.
This tool has been around for a bit and is used by some already. But since it popped up in my timeline a while ago (due to some updates) it just had to be added in this first edition!
Link: https://github.com/twintproject/twint
Info: Email to Facebook ID
In case you have a bunch of email addresses, and you want to try and find out which one is used by a Facebook account, there is a way of checking this in bulk. And it is all nicely explained in this article at Boolean Strings. Simply said: Prepare a text file with the email addresses, and follow a few simple steps where you upload that list as input for the "Find Friends" module of Facebook. It couldn’t be easier!

And since we’re at it, why not use that same list with email addresses to find some people on Twitter? If you already stopped to read the first article you might have a hunch as to what you will need to do here. But in case you need some extra explaining, no worries! Since Boolean Strings has you covered in the second article that was posted a few days earlier.
Facebook: https://booleanstrings.com/2018/05/06/...
Twitter: https://booleanstrings.com/2018/05/02/...
Website: CSE’s and more... (some offline)
CSE stands for "Custom Search Engine” and makes it possible for everyone to create a pre-filtered set of data and sites to get the best Google results possible. And there are quite a few of these custom engines out there! Earlier this month I was alerted about a list of some interesting CSE’s that were curated by Sprp77. A few days later followed another set of links and for good measure I also added a collection of medical sites under here. Thank you for sharing this with the community Stefanie Proto!.
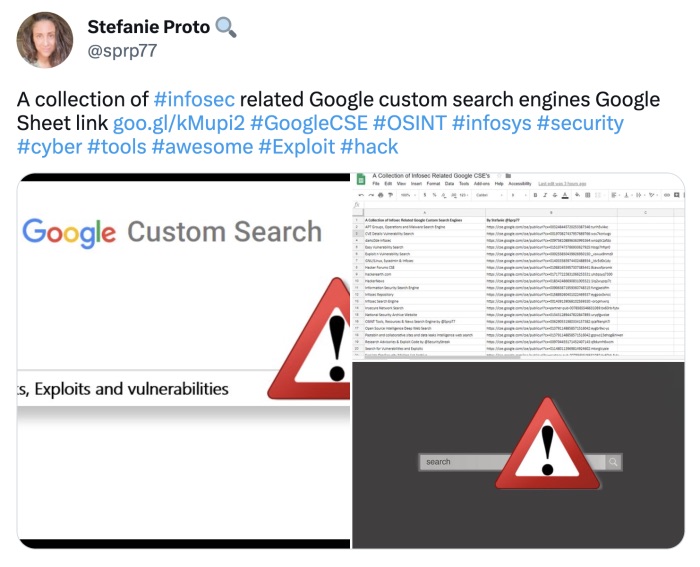
Here are the links. Sorry for the shortened links, but I really didn’t feel like putting the whole Google Doc link in here. But you are always free to check them all to see whether they are genuine, for instance at: http://www.checkshorturl.com/expand.php
Infosec related CSE’s (offline): https://goo.gl/kMupi2
Social media related CSE’s (offline): https://goo.gl/ms4H9K
Medical related sites: http://goo.gl/fPpZEY
And that was it for now! I will be taking it easy for a few days to relax a bit and after that, I’ll be back to hunt down more hints, sites, tools, or news about OSINT. And in case you have a tip, just drop me a message on Twitter or add me in a (re)tweet, and I might use it in the upcoming second edition of Week in OSINT.
Have a good week and have a good search!
