Google Calendar Spam
A new phenomenon that injects your Google Calendar with spam, a basic guide into a small investigation
Well, that was a first! I received a notification this morning that one of my many Google accounts had an invitation to uhm… Receive money? And it would repeat this for 30 days in a row, probably to make sure I didn’t forget to claim my money!
In this little blog post I am going to go over some basic steps most people can do if they want to investigate these kind of scams. I go over some easy to use commands and tools and at the same time I am trying to show where things eventually lead to.
It all started with the following notification on my phone:
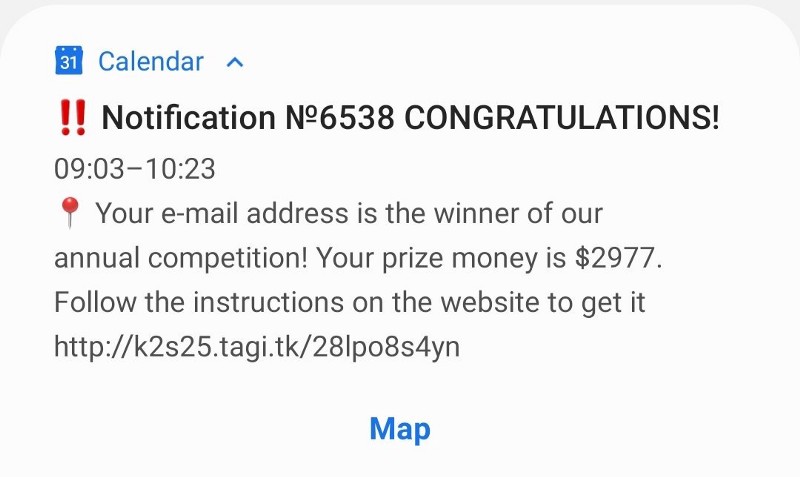
I opened the invitation in the Google Calendar, hoping that I was able to find some more information about the sender, but that didn’t really improve things either. This is a new — well, a couple of months old already — and upcoming scam that is not sent via an email address, but via scripts that use the Google API to create an invitation. Looking at the event, we only see the following information:
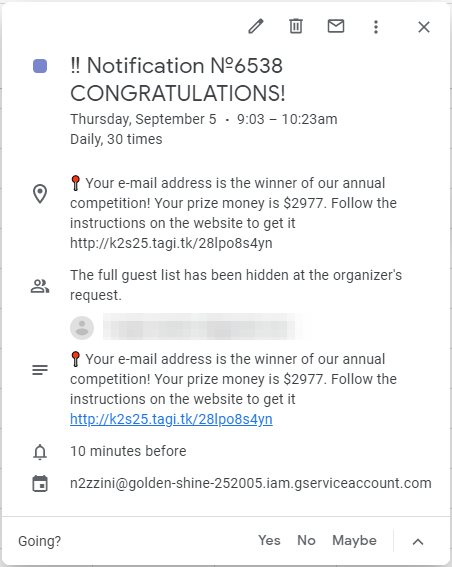
One of the first things I noticed what that it didn’t have a normal sender, but a weird and long URL on the bottom:
The first part “n2zzini” is the Service Account User within the Google project and “golden-shine-252005” is the name of the Google project itself. I quickly went over the the Google API documentation, but it seems that it is not possible for an outsider to retrieve things like the project owner or an email address. So the next thing I wanted to look at was the URL inside the calendar item itself:
hxxp://k2s25.tagi.tk/28lpo8s4yn
Usually one of the first thing I do when I see a URL is to see who the owner is of the URL and what is actually behind it in terms of a website and code. For people that are not so familiar with investigating things like this: DON’T OPEN IT IN A BROWSER! If the link is still active, you don’t want to be receiving digital gifts in the form of malware on your workstation…
Since most URL’s I encountered seemed to be completely hidden behind anonymous proxy services, I skip that part in this blog and concentrate on the content of the websites.
Unravelling URL’s
For tasks I will be using cURL or something similar, because it is able to retrieve information from the website, without running any scripts or for instance automatically downloading malicious files. I wanted to see the full header of the reply and the complete body — or content — of the website. If you want to read some more information about how to use it, then there is an article on OSINTcurious that explains how to use cURL. To retrieve the header and body, we can use the option ‘-v’:
curl -v hxxp://k2s25.tagi.tk/28lpo8s4yn
The reply didn’t surprise me to be honest. The web server returned the following data:
\* Trying 185.42.12.131...
\* TCP\_NODELAY set
\* Connected to k2s25.tagi.tk (185.42.12.131) port 80 (#0)
\> GET /28lpo8s4yn HTTP/1.1
\> Host: k2s25.tagi.tk
\> User-Agent: curl/7.58.0
\> Accept: \*/\*
\>
< HTTP/1.1 301 Moved Permanently
< Date: Thu, 05 Sep 2019 10:18:35 GMT
< Server: Apache
< Location: hxxp://mn42.ru/dk
< Content-Length: 225
< Connection: close
< Content-Type: text/html; charset=iso-8859-1
<
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>301 Moved Permanently</title>
</head><body>
<h1>Moved Permanently</h1>
<p>The document has moved <a href="hxxp://mn42.ru/dk">here</a>.</p>
</body></html>
\* Closing connection 0The output of the command consists of several different parts, where the lines starting with “>” are requests towards the web server, and “<” are the replies (called ‘response’) that are sent back to me. There are two lines important here, in the so called ‘HTTP Header’ of the response:
< HTTP/1.1 301 Moved Permanently
...
< Location: hxxp://mn42.ru/dkThe HTTP response status code 301 tells the browser: “Hey! The website is not here anymore, let me tell you how to automagically get there!”. And the other line that showed up a bit further up is called the “location response Header”. That gives the browser the new location that it needs to follow to reach the website that was ‘moved’, in this case ‘mn42.ru/dk’. So let’s go and curl that address too. And the result is…
\* TCP\_NODELAY set
\* Connected to mn42.ru (91.211.248.209) port 80 (#0)
\> HEAD /dk HTTP/1.1
\> Host: mn42.ru
\> User-Agent: curl/7.58.0
\> Accept: \*/\*
\>
\* HTTP 1.0, assume close after body
< HTTP/1.0 404 Not Found
\[ SNIP \]Okay, that didn’t help at all, it tells me that no website whatsoever was found on that particular address. Maybe it was already detected and removed? Or something else is going on, like me being a bit to sloppy? because what actually happened here, is that they probably detected that I am using cURL to retrieve the website (notice the ‘User-Agent’ above?) and refused to serve me the actual website. To impersonate a browser we can use cURL to send out a spoofed ‘User-Agent’ in the request, for instance a Firefox browser. A nice overview with ‘User-Agent’ values can be found here: https://developers.whatismybrowser.com/useragents/explore/
Sector035@X:~$ curl -v -H 'User-Agent:Mozilla/5.0 (Windows NT 5.1; rv:7.0.1) Gecko/20100101 Firefox/7.0.1' hxxp://mn42.ru/dk
\* Trying 91.211.248.209...
\* TCP\_NODELAY set
\* Connected to mn42.ru (91.211.248.209) port 80 (#0)
\> GET /dk HTTP/1.1
\> Host: mn42.ru
\> Accept: \*/\*
\> User-Agent:Mozilla/5.0 (Windows NT 5.1; rv:7.0.1) Gecko/20100101 Firefox/7.0.1
\>
**< HTTP/1.1 302 Found**
< Date: Thu, 05 Sep 2019 11:07:36 GMT
< Server: Apache/2.4.25 (Debian)
< Access-Control-Allow-Origin: \*
< Set-Cookie: cu\_dk=0; expires=Fri, 06-Sep-2019 11:07:37 GMT; Max-Age=86400; path=/
**< Location: hxxp://link24.org/wcf7**
< Content-Length: 0
< Content-Type: text/html; charset=UTF-8
<
\* Connection #0 to host mn42.ru left intactThere we have it! We found another HTTP error code, now it is a 302, which is a ‘redirect’. That means that the browser is directly being sent to another URL, in this case ‘link24.org/wcf7’. Following that link, we see that we finally get somewhere, but simply downloading and checking a bunch of source code that was retrieved via cURL isn’t the most easiest option. Since I wasn’t too keen on using my own browser to do more recon, it was time to fire up a cool online service called Any.run!
Sandboxed Sessions
Any.run is an awesome online platform where you can investigate URL’s you don’t trust, specially when you suspect malware. They provide you with a safe and sanboxed environment, where you can safely open URL’s while you browse a web page for a short amount of time (default is 60 seconds). In the meantime it will record everything you see and saves all the communication that happens in the background.
Using this service, the URL served me a website that displayed some kind of scheme about winning a prize, and below the browser screen there you can find all the other requests that were sent by the browser, connections and other information. It rewrites the URL in the browser to ‘xiveth.xyz’ and it shows is the following page:

Within the browser I scrolled down a bit it and I was presented a big, bulky and blue button. If I wanted to collect any money, I first hat to ‘confirm my participation’. Woohoo! I was getting really excited here! Well… Not really…
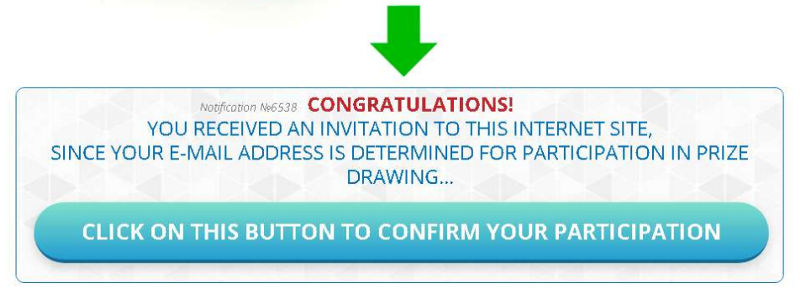
So there I was, clicking the button and adding a few minutes to the run time. Then it told me it was a bit busy… No, really! These tings aren’t as fast as you think! We have to be patient and wait…

After this screen we seem to get into a ‘click an answer’ kind of game, where for some unknown reason they really would like to know:
- What email provider we have (Google, Yahoo etc)
- What email program we use (Mailbird, TheBat etc)
- How we usually view our email (browser, smartphone etc)
With each question I clicked a random answer and after each I was ‘rewarded’ with another waiting screen. And then after a little bit of extra waiting I was finally able to start finding out what prize I won!

Oh wait… More random clicking and going over stupid screens… After another few minutes and clicking coins three times and ‘winning’ […] some money each time, I found out I was going to be rich! And I mean, I was going to receive the nice sum of close to $25.000 in winnings! But wait a minute… I just ‘WON’ this $24.850 by clicking these coins, but what happened to the rest? The initial $2997 that I won? 🤔
Never mind, let’s continue and see what it says…
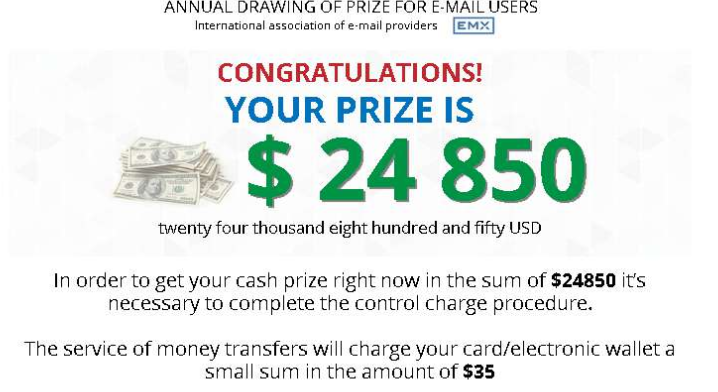
So there it is, the scheme that finally presents itself! We first have to pay a small sum of $35 for
And that was it, a little read into how you could use some basic online tools to investigate possible scams or malware. But wait a minute… Is that really all there is to it? Well… Not really.
Eerie Extensions
When I went over all the URL’s that were opened or contacted by the browser, I found that there was one specific request that I needed to check. The full URL that can be seen in the network traffic is the following:
<HTML>
<HEAD>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<TITLE>302 Moved</TITLE>
</HEAD>
<BODY>
<H1>302 Moved</H1> The document has moved
<A HREF="http://r4---sn-aigzrn7s.gvt1.com/edgedl/chromewebstore/
L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/
7519.422.0.3\_**pkedcjkdefgpdelpbcmbmeomcjbeemfm**.crx?
cms\_redirect=yes&mip=185.217.117.161&mm=28&
mn=sn-aigzrn7s&ms=nvh&mt=1567685362&mv=m&mvi=3&
pl=24&shardbypass=yes">here</A>.
</BODY>
</HTML>I emphasised the most important part in this URL, since I immediately recognised it as a unique identifier for a Chrome extension (and the rest of URL helped here too I must say). I could have downloaded this extension, may have spent some time looking over it, to try and see what it did, but in such cases there are loads of people much smarter than me when it comes to this.
So I decided to simply try and find out whether this was an already known extension. Google is your friend after all (well, you know what I mean) and soon after I found loads of posts about this particular extension, and it seems to be a modified version of the ‘Chrome Media Router’. Do notice the word ‘modified’, because this slightly enhanced version has something extra.
According SecureList this little piece of $*#@ — I mean, unwanted software — is able to look for Bitcoin addresses within the text of a website or QR codes and modifies it with bitcoin addresses of their own. So besides serving you a money winning scheme, where they try to lure people to pay up a small amount of money to get their non-existing prize, they serve the other people a piece of software that is able to trick you in other ways at the same time.
Conclusion
Schemes are as old as human civilisation and I doubt we’ll ever get rid of these things. Now that everything has to be ‘online’, there are so many more ways to trick people into sending money to crooks. So please, be careful out there!
I conclude my little search here, since I really didn’t want to go over all kinds of the IP addresses, Whois information behind proxies, the involvement of the Dutch company Freenom that owns the top level domain .TK or the Ukrainian company that owns the IP address 91.211.248.209. Something else that might be interesting are other shady domains like ‘e-pay.click’ and ‘e-pay.marketing’ that I encountered, but I didn’t have time for all these things…
So there it is! A little look into what simple steps you can take to investigate a domain that is serving you malware, or tries to scheme you from your hard earned money.
For the full analysis, the Any.run report can be found here.
The sandboxed browser session with all the screen shots is here.

Curious about that email address? Well, I wasn’t the only one receiving the $24.850, there were more… I’m less unique than I thought.
