Week in OSINT #2024-29
Welcome to a short update of week 29 of 2024, where I dive into some interesting posts I found on social media.
Last week I had an extremely busy weekend, where I hardly had any spare time for myself, so I really had to skip that one! But slowly we're getting things bak on track, so this week I really needed to share a few interesting topics. I had some more items I wanted to touch, but yeah... Then the whole world imploded when Crowdstrike pushed an update, that halted everything from ATM's to airports. So that were a few interesting days, especially seeing how automated our world is, and how one 'tiny' error (...) can stop our society. And that also shows the importance of staying vigilant about cyber attacks and digital threats. But that's enough rambling for now, it is time for the few topics I picked out for this week:
- BigDomainData
- OSINT4All Start.me
- urlDNA
- Micah's Resources
Site: BigDomainData
Everybody knows Whoxy, when it comes to retrieving historical Whois information. And until some time ago there was DomainBigData, but sadly that has stopped operating. But while I was doing a research project on my own, I actually found a similar site. With BigDomainData, you have a large database of historical Whois data to your disposal. And even though Whois records are mostly redacted due to GDPR laws, it can still give an indication whether a domain name has been transferred or not, since usually the city and country are still visible. So when a long running domain name hasn't moved from the location after being redacted, you may actually have an indicator who the current owner is. And with this site, it isn't just historical records, but they also offer a reverse search on all sorts of Whois records too.
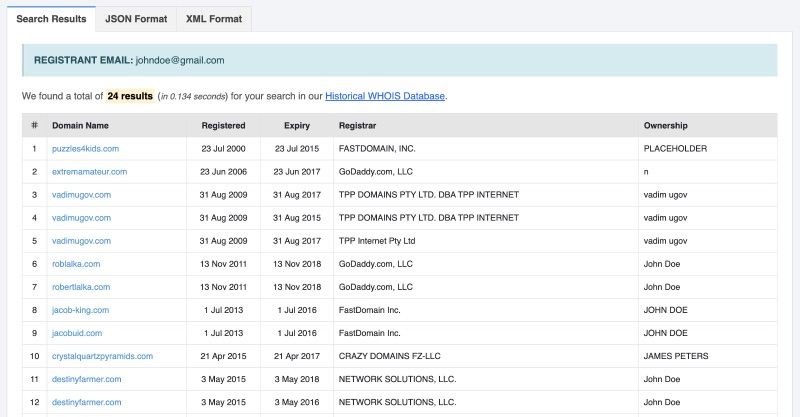
Link: https://www.bigdomaindata.com/
Links: OSINT4All Start.me
This StartMe page is several years old already, but it is almost impossible to collect them all! So here is another one for you to have a look at, and see what resources are available in there. It is still being updates, with the last update around 2 months ago at the time of writing, and contains loads of different categories for you to explore. It is still a mystery to me why it was never featured though, since it has been the most visited StartMe page several times in the last few years. Time to continue this I think
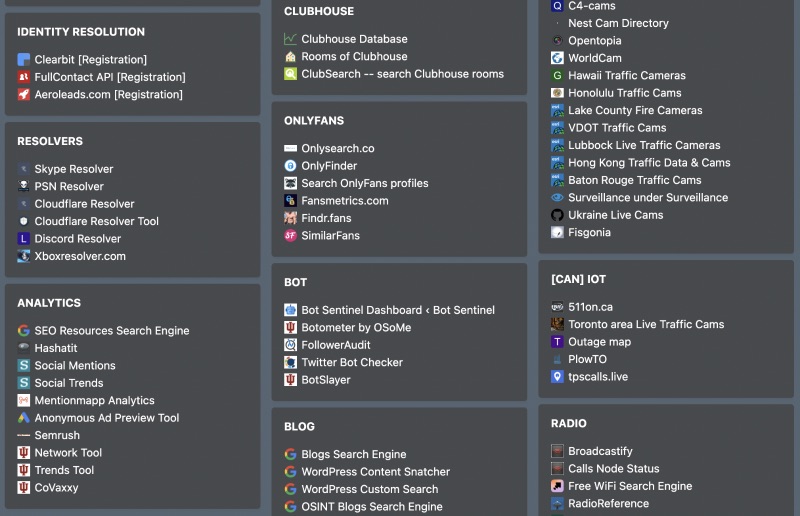
Link"https://start.me/p/L1rEYQ/osint4all
Site: urlDNA
Last week I was notified by 0xtechrock [] about a new online service, called 'urlDNA' [ ]. It is an online platform is able to scan malicious or suspected phishing sites, and has a wide range of query options available. It can be used for brand monitoring, query on similar sites via favicons, screenshots, or infrastructure, and a lot more. It gives you an online sandbox and it can scrape new sites via their Python library. And the best part of all, it is all free!
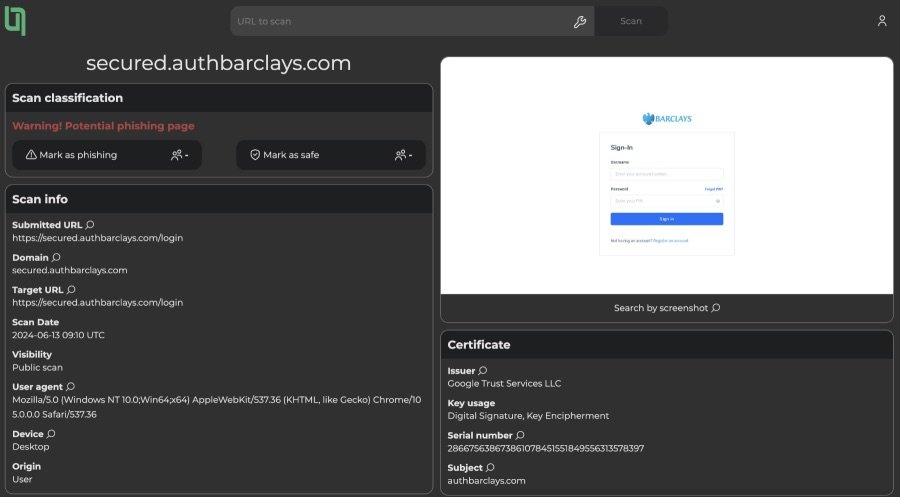
Link: https://urldna.io/
Blog: https://medium.com/@urldna/...
Links: Micah's Resources
Staying on the topic of DNA, this man has OSINT embedded in it I think! He has been a mentor for a lot of people over the years, and many have seen him teach SANS classes, or are enjoying his current online content. Micah Hoffman [ ] has developed multiple tools and techniques over the years, and on this page he shares them with you. Pretty much all of his resources have been featured in WiO before already, but for some this might all be new. So go over, and check out the free content, and do make sure to check out his course material too!
Link: https://www.myosint.training/pages/free-resources
FUNINT: This Week's Meme
When you have a background in infosec, and also really want to spend time on keeping up with a personal blog...

Have a good week and have a good search!
