Week in OSINT #2022-41
This week I dive into some audio, OpSec, Telegram, a tool to investigate domain names via the Internet Archive, and a TryHackMe challenge.
I struggled to get this one live in time, not because there wasn't enough to share, but simply because I was too busy having fun, without thinking about anything OSINT related! I've been way too busy the last couple of weeks to enjoy some time off, so it was about time to enjoy some great food, some good company, and have some time off. For this week, I've looked at the following topics:
- Audio
- OpSec and VPN
- Telepathy
- TheTimeMachine
- Shodan TryHackMe
Article: Audio
Nico Dekens has written a blog post about investigation audio, for instance background noises in a video. He describes what to listen to, he lists some handy tools to process audio, tools that can help identify sounds, and he even added an audio file to practice. Audio can play an important role in geolocating a possible video, especially when there are sounds that can point to certain locations. You are not sure how that might help? Then download the audio file from his blog, and have a try at it!

Link: https://www.dutchosintguy.com/post/audio-osint
Article: OpSec and VPN
For several years already it has been known that bot Android and iOS don't always respect the privacy that comes with running a VPN client. Both these operating systems actually circumvent the VPN connection, mostly when contacting their own services. This might result in leaking of information, for instance leaking of DNS requests. For most users this might not be a big deal, but when you are working with very sensitive topics, I would really suggest to not simply run a VPN client on your phone, but connect it to a router that tunnels all incoming requests through VPN. Thank you mysk_co for researching iOS 16 and sharing this news.
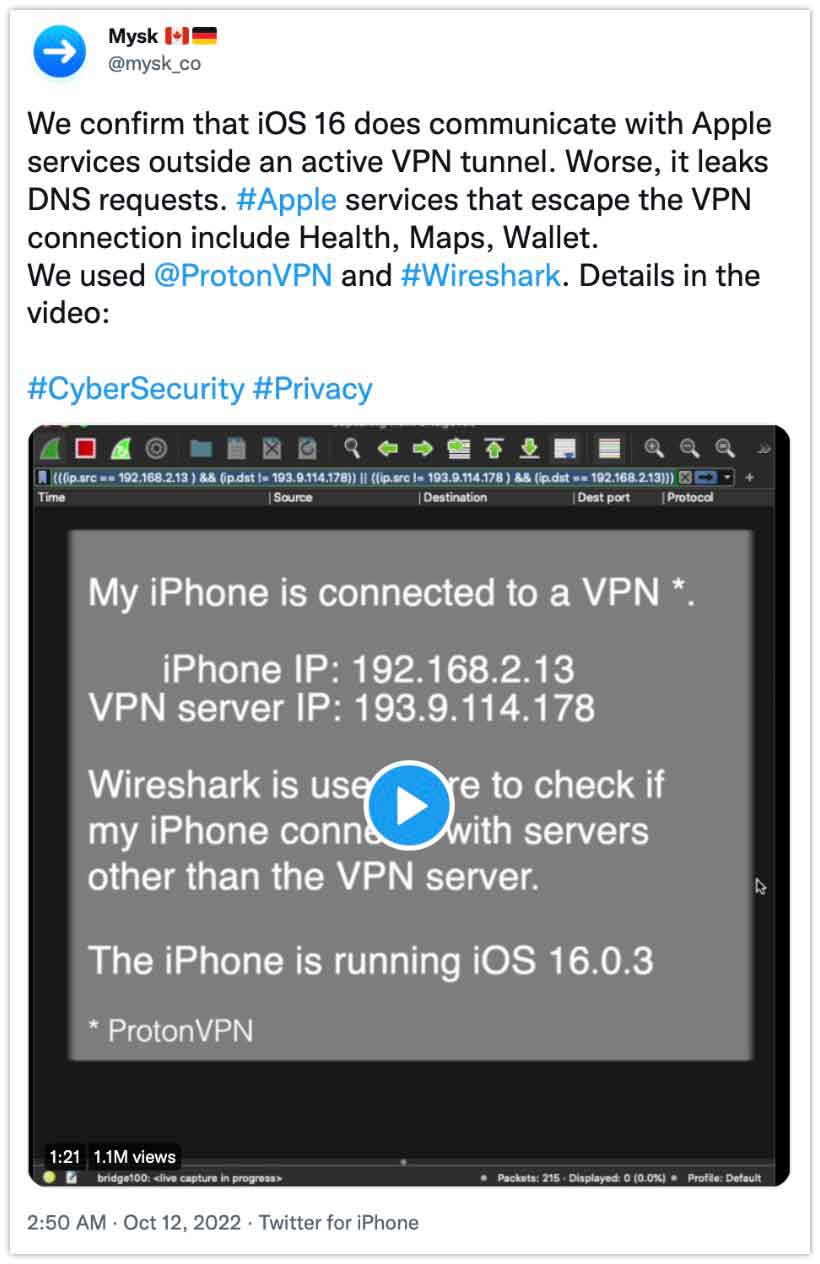
iOS: https://www.cnet.com/tech/...
Android: https://mullvad.net/...
Tool: Telepathy
Jordan Wildon has enhanced his Telegram tool Telepathy with multiple features, that are highlighted in this blog post by os2int. The most notable feature that is added, is the location-based search. With this feature it's possible to search for users within certain areas around any given coordinate. Another great addition to this Swiss army knife of Telegram tools!
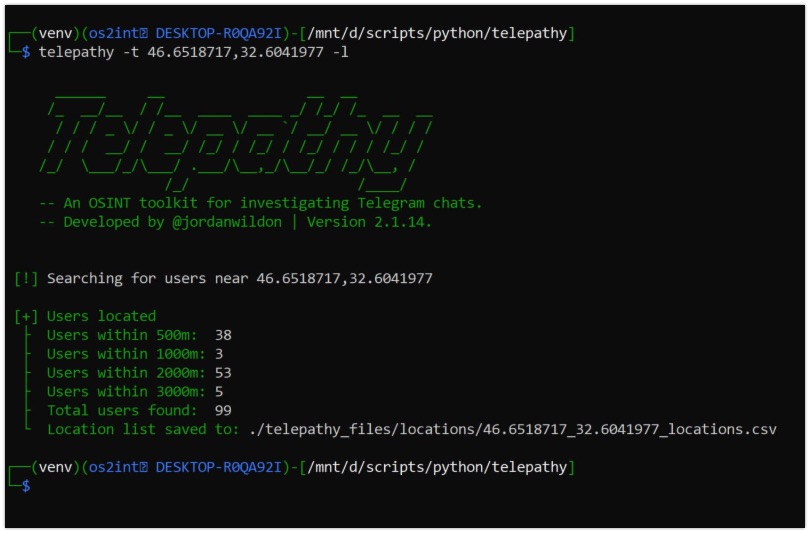
Blog: https://os2int.com/toolbox/...
GitHub: https://github.com/jordanwildon/Telepathy
Tool: TheTimeMachine
This tool by FR13ND0x7F was developed for bug bounties, but when you are somewhat technical, and you know what the tool does, this is a handy tool to have. It scrapes the Internet Archive and dumps all URLs from a given domain into a text file, and identifies subdomains that are available. From the scraped content it can also identify API or JSON endpoints. A small, but handy tool when working with domain names. Thanks for the tip cyb_detective!
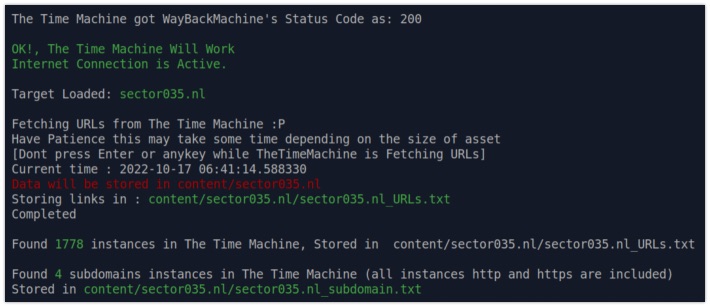
Link: https://github.com/anmolksachan/TheTimeMachine
Tip: Shodan TryHackMe
Talking about domain names and related things, are you looking for some extra practice? Why not jump over to TryHackMe, and have a look at the Shodan room created by 0xbee. Go over the questions one by one, and discover the different aspects and possibilities of Shodan, and get a deeper understanding on how to query the service. Thanks for creating this!
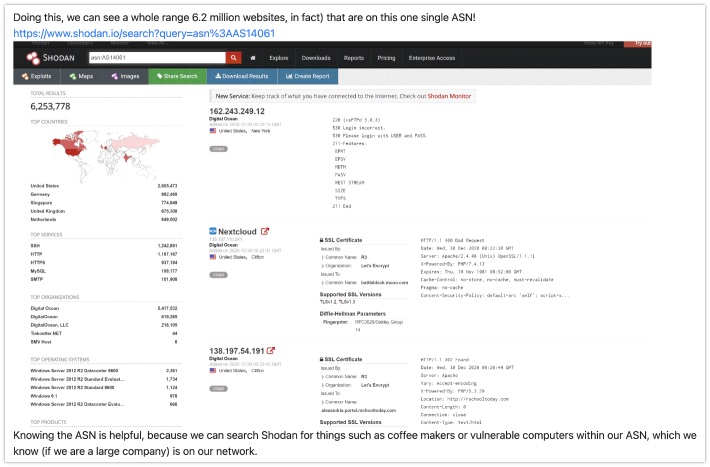
Link: https://tryhackme.com/room/shodan
Have a good week and have a good search!
