Week in OSINT #2022-04
This week it's a really filled episode on topics ranging from captured pages to OpSec in TikTok!
What a week it has been! So many awesome things that were shared with me, and so many topics I really wanted to write about, but so little time. I'm happy that I managed to find enough time to write about some very interesting topics. Again I learned a lot of new tricks and found new topics to dive into, like the news media run by the GRU, or a new plugin for Maltego. Thanks for sharing all these things with the OSINT community, so I can collect them and give you my view on the following topics:
- URL Shorteners
- Ginger__T on Telegram
- Maigret and Maltego
- Archived Pages
- GRU's Galaxy
- AHREFS and Backlinks
- State of OSINT
- Polycam
Tip: URL Shorteners
It's been some time ago that OSINTtechniques gave some tips on how to view the link behind a URL shortener (link to original tweet). Many of these services have some way of previewing the link behind it, and else there are services that can show you where a link will lead you, here's a small overview of some of the most used services:
| Service | Info |
|---|---|
| Bitly.com | Add + at the end |
| Cutt.ly | Add @ at the end, or visit https://cutt.ly/preview and turn on preview mode
|
| Goo.gl | Add: + at the end |
| Is.gd | Add - at the end |
| Tiny.cc | Add = at the end , or ~ for statistics |
| TinyURL.com | Add preview. in front of the URL |
If you want to use a third party platform to follow the link, the do look at the last item in my Week in OSINT 2021-16. And even more services and how to preview their links can be found in an awesome cheat sheet that is curated by @SEINT_pl.
Cheat sheet: https://seintpl.github.io/osint/...
Article: Ginger__T on Telegram
@Ginger__T wrote an article on Telegram, where he talks about some features, research options and the OpSec of having a Telegram account. He also discovered a new feature that slipped past me: The new in-app translate feature of the latest Telegram clients.
I have completed a new #OSINT Blog Post - Telegram Fundamentals - Watch out for false negatives, https://t.co/kqhcSdrLol pic.twitter.com/jhNhqBgTxu
— Ginger T (@Ginger__T) January 27, 2022
Link: https://www.cqcore.uk/telegram-fundamentals/
Tool: Maigret and Maltego
Twitter user @OS2INT wrote about a new local Maltego transform: Maigret. The article didn't specify how to install it, but a little search led me to the original GitHub page from the awesome @Soxoj. After installing it into Maltego, it was a breeze to run it! Another awesome local transform for Maltego, even if it comes with a lot of false positives.

Link: https://github.com/soxoj/maigret-maltego
Os2Int Artcile: https://os2int.com/toolbox/...]
Tip: Archived Pages
Jordan Wildon shared an awesome tip on Twitter, showing how to retrieve all the captured pages of a specific URL and it's subpages from The Internet Archive. In his example he used a Twitter profile, but this can be tweaked to anything you want. I changed the example he showed slightly, to only show tweets and nothing else.
https://web.archive.org/web/timemap/?url=https://twitter.com/{UserID}/status&matchType=prefix&collapse=urlkey&output=json&fl=original,mimetype,timestamp,endtimestamp,groupcount,uniqcount&filter=!statuscode:[45]..&limit=100000Let's have a look at everything that's inside this URL, by going over the options that I found over at GitHub:
| Item | Explanation |
|---|---|
| web/timemap/ | An overview of all archived 'Mementos' and their date (RFC 8079) |
| matchType=prefix | Return all matches that have the same URL path that was provided |
| collapse=urlkey | Only return unique URL's, even if there are multiple captures |
| output=json | The output format, if removed it returns just a list of URL's |
| fl=original | Field order, where original defaults to alphanumerical order |
| mimetype | Will include the type of content, ie: text/html, application/json, unk(own) but it's quite useless here |
| timestamp | Show the timestamp of first capture |
| endtimestamp | Show the timestamp of latest capture |
| groupcount | Total amount of captures for the URL |
| uniquecount | Amount of unique captures for the URL |
| filters= | A set of filters, they follow right after this |
| !statuscode:[45] | Don't show pages matching a specific HTTP error code. This is probably a typo, since HTTP error code 45 doesn't exist. Maybe this should be: 404, meaning 'page not found' |
| limit=100000 | Maximum amount of results to return |
Article: GRU's Galaxy
Openfacto published a report on more than 1300 online news portals that seemed to be connected to the GRU, the Russian intelligence service. The report not only explains how the websites were found, but also give insight in the very timely registration of domain names, their content and the location of the 'target audience'. An interesting and well written report from this organization.
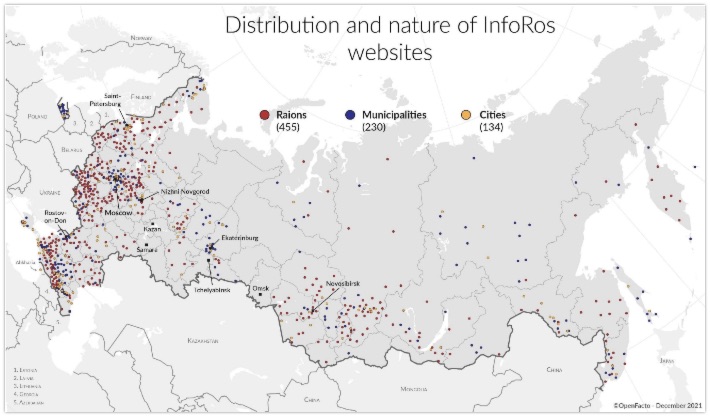
Link: https://openfacto.fr/2022/01/27/...
Tip: AHREFS and Backlinks
Twitter user @UnleashedOsint found out she could buy access to the vast amount of data inside AHREFS. When going over the 'backlink' section, it was evident that there is lots of information that could be gained about Telegram, and surely about other platforms that are tracked too. Interesting thread of tweets here
#Telegram #Security #OSINT
— osint_unleashed (@UnleashedOsint) January 26, 2022
A Thread
Out of curiosity wanted to see if all backlinks for Telegram are openly attainable-they were offered to me by AHerfs Backlink checker for $7 USD. It appears that is indeed the approx cost, I think some are missing- provided with over 27 MiL pic.twitter.com/bVC34YqaVJ
Twitter thread: https://twitter.com/UnleashedOsint/status/1486304518254075904
Site: State of OSINT
Last year the State of OSINT was launched, and this year they're back. @Ginsberg5150 has gathered a team of experts that share their 2021 highlights, talk about trends and tools, and the changes within the OSINT landscape. The interviews are a good summary of the state of OSINT within different areas of expertise.

Link: https://stateofosint.com
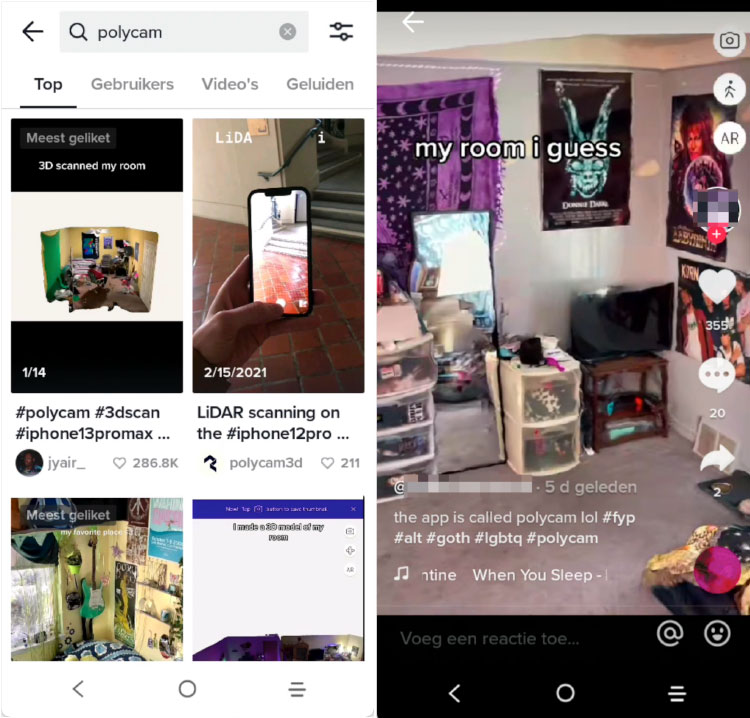
Tip: Polycam
An upcoming trend seems to be the usage of LiDAR in iPhones to create a 3D view of locations, with the use of Polycam. This is an interesting development and besides it being an opportunity to view inside people's homes, it wouldn't surprise me that at some point such a video will turn up in an investigation. Thanks @Zewensec for pointing out this new trend!
Have a good week and have a good search!
