Week in OSINT #2021-40
Welcome to another mishmash of open sources, tools and articles. This week it's about international crimes, social engineering, books, tools and more!
The amount of tips and links didn't stop this week! I've written it before, I'm sometimes still amazed by the amount of new content I'm able to share, even after over three years of writing this weekly newsletter. So much to learn, and so much to share! So grab yourself that Monday morning coffee, and let's kick things off with the usual overview:
- Investigation of International Crimes
- About Fraudsters and Social Engineering
- OpenCorporates CLI
- Threat Intel in SpiderFoot
- OSINT Map
- Advangle
- OSINT Books
- Hunchly and Maltego
Article: Investigation of International Crimes
Alexa Koenig shared a link last week to a journal that is released for free, for a 60-day period. I haven't read everything yet, but please do take your time to read this if you're into investigating international crimes. They go over preserving evidence of international crimes according to criminal justice standards, and there's a discussion about the efficacy and ethics of sexual violence investigations. It touches the problems with cognitive and technical biases, they cover the experiences on the use of the eyeWitness app, and its evidence used in court. But also the challenges and lessons learned of using digital evidence in the International Crime Court, with its own laws that aren't always suited for digital evidence. All in all a huge read, well over 200 pages, but I think it's very important for everybody involved in this line of work.

Link: https://academic.oup.com/jicj/article/19/1/1/6314899
Article: About Fraudsters and Social Engineering
Twitter user Ithaka32 shared an article by the Guardian explaining how fraudsters use information shared online to social engineer people. It's a growing concern, where people are being tricked into sending off their money to criminals. Despite the fact that Hilary Osborne wrote the article for their public, and not so much for my OSINT-geeky readers, I think it's important to share stories on the darker sides of using open source information. Stay ethical and stay safe. Not only because it's the right thing to do, but the chances of being caught are very real.

Link: Article at the Guardian
Tool: OpenCorporates CLI
Over at GitHub, Richard Mwewa has created an unofficial command line tool to OpenCorporates. It's a very simple tool to use, and only has a few basic options. It dumps all the information it can find on a company name, you can dump it to JSON and has the ability to write it to a JSON file. Despite it being limited in its options, this is a very handy little tool to include in other platforms, code or when you work with company data, and you have the need for large data in JSON format.
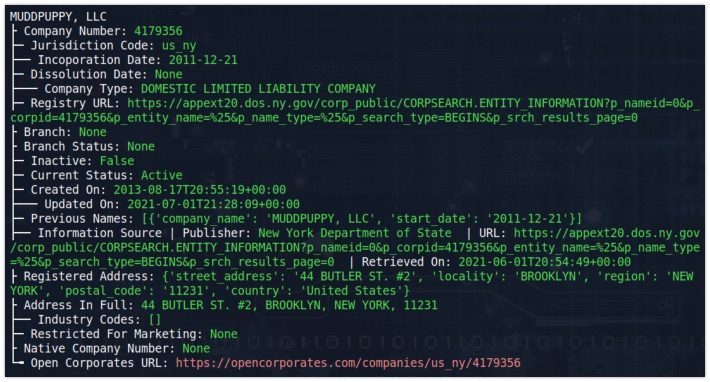
Link: https://github.com/rlyonheart/occli
Article: Threat Intel in SpiderFoot
Over at SpiderFoot they asked hakluke and dccybersec to collect a top 5 of threat intelligence resources. There is a lot of information out there, but the 5 chosen platforms are absolutely among my favourites too. A wealth of information if you ever have to deal with malicious IP addresses, and the best part of it all: Most of these platforms are free, or offer a free tier.
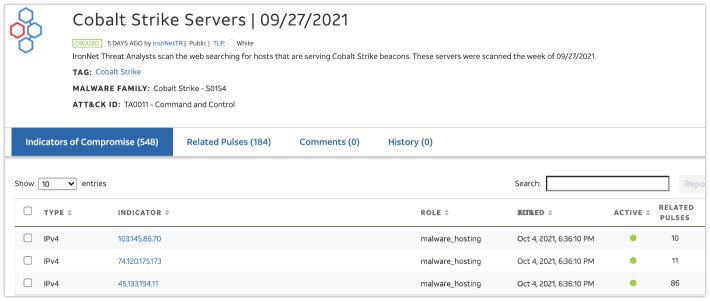
Link: https://www.spiderfoot.net/...
Site: OSINT Map
One of the most active Twitter peeps sharing OSINT resources out there, is cyb_detective. And he's published a new tool, the OSINT map. Over two years he has collected links about public transport, business registries, vehicle information, cadastral maps and such, and has now plotted them on a map. Lots of countries are added, but some are still missing links, so feel free to add them to his GitHub repo. Thanks for creating this map, and keep up the good work!
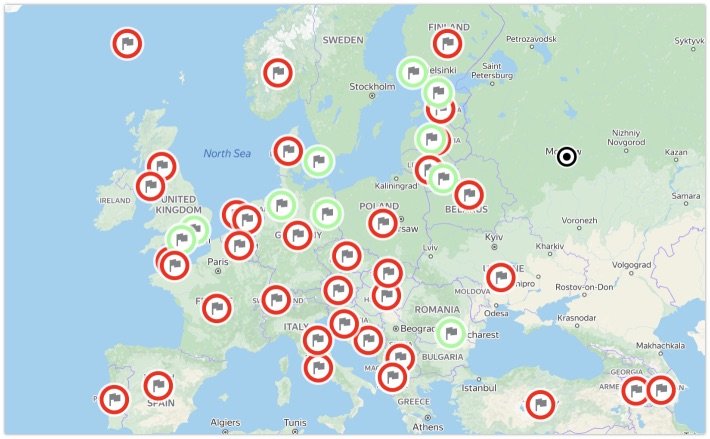
Link: https://cipher387.github.io/osintmap/
Site: Advangle
An awesome tip was shared by Ritu Gill this weekend. The website Advangle is an online tool that helps you create Google and Bing search queries via interactive menus. After being built in 2013, it finally found its way to my weekly newsletter. By the looks of it, it hasn't even been updated since then, and doesn't even have a secure connection over HTTPS. But if you're a bit new to writing complex search queries, or you like to visualize your searches, this website is a must. Simply add your conditions and attributes one by one, and click the search engine you want to query.
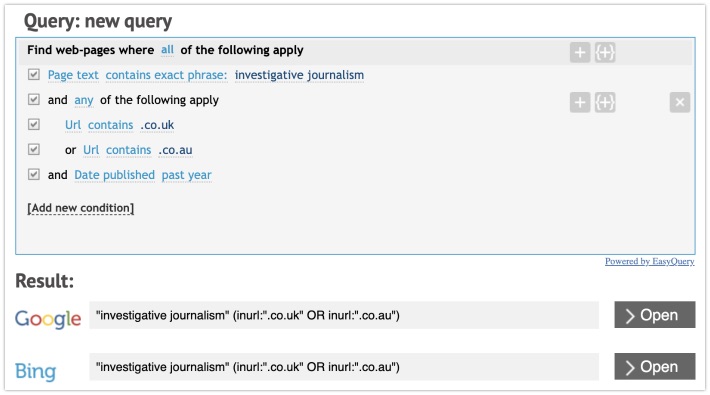
Link: http://advangle.com/
Tip: OSINT Books
Maltego is sharing tweets this month with the hashtag #OSINTOctober, and every day there's a new tip, link or site they share. On Saturday they shared a list of books that are a must-read for OSINT enthusiasts. Keep an eye out on their Twitter feed, because there's a lot more interesting things to come!
#OSINTOctober - D9 | Top 7 #OSINT books you must read:
— Maltego (@MaltegoHQ) October 9, 2021
1. Cybersecurity Blue Team Toolkit
2. Human Hacking
3. Nowhere to Hide
4. OSINT for the Staffing World
5. Operator Handbook
6. Open Source Intelligence Handbook
7. Practical Cyber Intelligence pic.twitter.com/H5uLDoCy4K
Link: Tweet by MaltegoHQ
Media: Hunchly and Maltego
Talking about Maltego, did you know that Hunchly has some Maltego transforms that enables you to import a Hunchly case in the tool? After importing a case, all the captured pages, images, selectors and objects are available to be used within Maltego. This makes it possible to get a visual overview of all the captured data, and run transforms on the data you've already gathered. A great tutorial by Justin Seitz, and I recommend you to watch this if you work with both of these tools.
Link: https://youtu.be/ZtZZEDcIRw8
FUNINT: Shodan Fun
Back in 2019 I was honoured to give a talk about OSINT and operational security fails over at Europol in The Hague. I covered things from personnel passes to industrial pumps, and from sensitive information in digital certificates to credential leaks. This image was just one of the more funny examples I included in my talk, and I was reminded of it when I spotted something similar online last week. My question for you is: What is the most funny Shodan screenshot you ever found? Share it via Twitter using the hashtag #ShodanFun!

Have a good week and have a good search!
