Week in OSINT #2021-27
This week I've got some nice links and tips, but for some weird reason more than half of this newsletter is about Tor and I2P.
When I saw the link to the TorWhois website last week, I immediately though about some other resources that were known to me for some time, but that I never shared in this newsletter. This makes this episode not just a 'week in OSINT', but actually a little view inside my mind, my own resources, and what I'm mostly into: OSINT on the technical site of the internet. I think it's a good idea to share these, since many resources are being shared already on Twitter and other social media. So when I'm able to share information that hasn't flooded your screen in the last few days, it's slightly more interesting. This also explains why I only thanked a handful of people in the accompanying tweet this week. Anyway, enough rambling, it's time for this week's overview:
- Telemetrio
- Screenshots in Browser
- Intro into Dark Web
- TorWhois
- ExoneraTor
- I2P Search
Site: Telemetrio
Ben Heubl shared this site some time ago, and I somehow missed his tweet back in April. Telemetrio is another Telegram indexing site, and although it misses loads of messages and isn't up-to-date with the latest content, it does have a huge amount of channels that are tagged by category, language and country. It also keeps track of deleted content (if indexed), and even has some private channels and groups. It isn't perfect, for instance the top result in the screenshot is Spanish and not English like I requested, but this is just another large resource if you're looking for specific channels or groups.
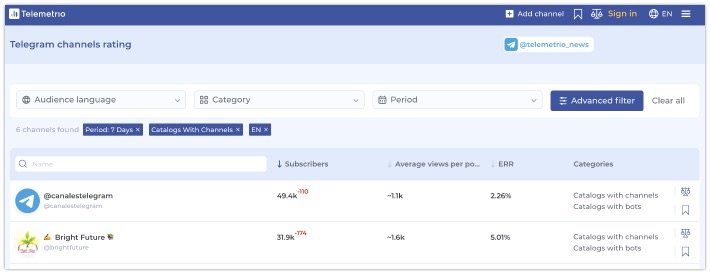
Link: https://telemetr.io
Tip: Screenshots in Browser
OSINT Combine shared an awesome tip last week, about taking screenshots in a Chrome browser without the need to install an extension. Since a specific set of extensions can be used to fingerprint a browser, this can be helpful if you want to stay private. And the more extensions you have, the more likely you have something installed that might be unsafe. To use this, do the following:
- Open the developer toolbar (Ctrl-Shift-I or Opt-Cmd-I)
- Make sure you are not in the tab "Console" (important!)
- Run command (via menu, Crtl-Shift-P or Cmd-Shift-P)
- Type
screenshotand select your action
The good new is, that this is also available under Firefox. For this, the workings are similar. For this you open the developer tools, and make sure the 'split console' is visible. This will give you a small area where you can type in commands underneath the current tab you're on, for instance:
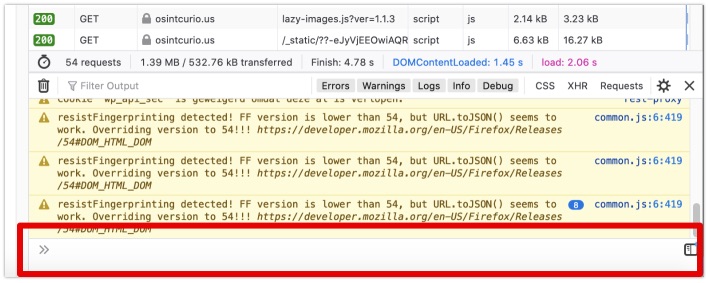
In here you type a colon, followed by the command you need, in this case screenshot. After pressing the enter key, it'll create a screenshot if your current screen. But also here there are a few options available for you:
:screenshot --fullpage
:screenshot --fullpage --clipboard
:screenshot --selector “.video-player”The selector options gives you the ability to create a screenshot of a specific element on a page, like a <div>, a <span>, or any other HTML entity that has a class. This may not be the easiest option if you're not into HTML codes though. And if you want it even easier, you can even customize your toolbar and add the screenshot button to Firefox.
One import warning though! Firefox does collects some data about their screenshots, so make sure to read up on that and opt-out if you're not comfortable with that.
After making a screenshot, both Firefox and Chrome will tell you that the file is saved, and by default it'll be placed in the download folder of the logged-in user.
Article: Intro into Dark Web
Before going to this week's topics, I'd want to share an article by Huntress' Rachel Bishop. Since anonymous and decentralized networks like Tor, I2P, Freenet, ZeroNet and many others might still be something scary for some people, this article will help you understand it's not much different from the surface web. By showing examples of what can be found in, for instance, dark markets, she explains how similar the experience is with regular websites. I had a great time reading it, and I'm actually curious about Rodrigo's story now too...
Link: https://www.huntress.com/blog/pulling-back-the-curtain-a-journey-through-the-dark-web
Site: TorWhois
The Twitter user OSINT Stuff has been sharing tips for quite some time now, and last week he tweeted out a site that has been around for years but that I somehow missed before. To make it clear: The website TorWhois is actually not a Whois service, so don't expect to retrieve any registration information! What it is, is a search engine that has scraped HTTP headers of Tor-sites, and gives you the option to search for a domain or keyword within these headers. Some cons though: It only retrieves 10 results at a time, you can only search for a single keyword, and there are no search operators available as far as I was able to check.
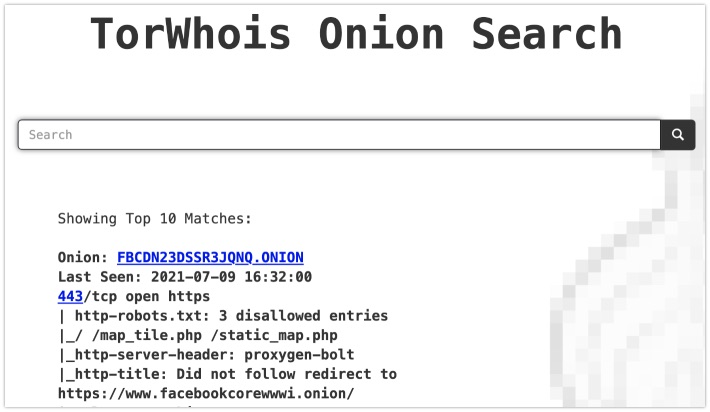
A really useful option is the option to search from the command line. By querying them as a normal Whois server, you are able to retrieve the scraped HTTP headers from the command line, for instance:
whois -h torwhois.com FBCDN23DSSR3JQNQ.ONION
Even though it responds with the same output as shown in the web version, it's a lot easier to use in scripts, or parse it for other purposes.
Link: https://torwhois.com
Site: ExoneraTor
Speaking of the Tor network, most people that are somewhat tech-savvy and have used Tor before, know that the Tor Project keeps track of Tor nodes, or relays. They actually provide a simple search engine, where you can check whether an IP address has been seen as a Tor node at a specific date. So if an IP-Whois website like IPinfo gives you a green tick for a Tor node, do visit this site to verify that claim, just to be sure.
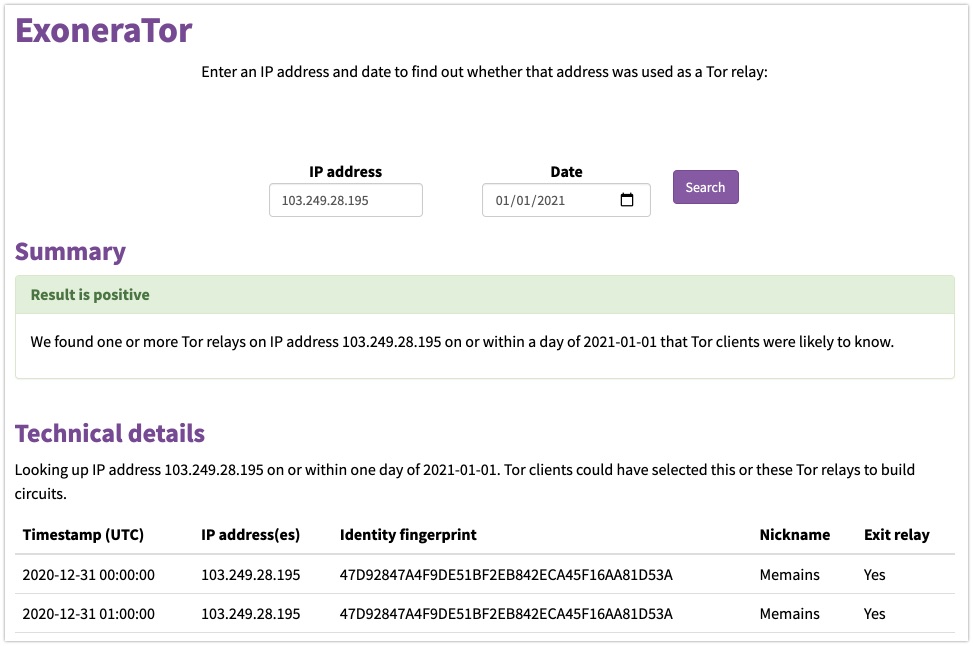
Link: https://metrics.torproject.org/exonerator.html
Search: I2P Search
From the makers of OnionLand Search, there is another search engine, designed for 'eepsites', or I2P sites. These are websites operating on the Invisible Internet Project, or I2P for short, and is comparable to Tor when it comes to its use and philosophy, but operate on a different technical level. Addresses of I2P sites are more difficult to find, since there are fewer services online dealing with this network, so this search engine is a very welcome resource!
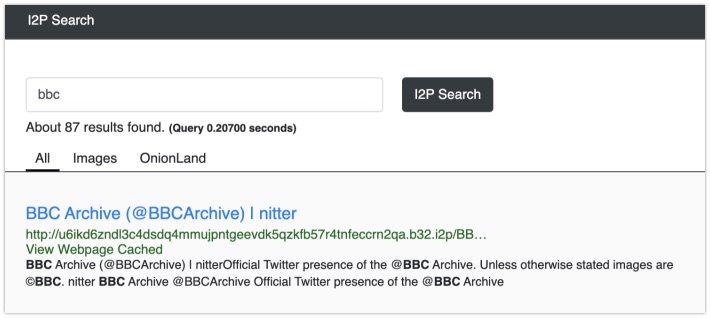
Link: https://i2psearch.com
Have a good week and have a good search!
