Week in OSINT #2021-19
Are you in for a treat? Looking for content that hasn't been retweeted last week, or have been shared much by the community? Well, I've got you covered this week!
Last week I've been browsing around a bit and was able to find some interesting articles, sites and tips. And the cool thing is, I learned a lot myself too! I didn't know what kind of footprint North Korea had online, but I'm keen to find out myself too now. I also found an interesting resource for Overpass Turbo that I've been using already. I also removed a link on Instagram posts from my website because it's offline, but three new sites took its place! This and more in this week's episode:
- Hunchly Mobile
- Clint Watts
- Instagram Tools
- Browser Fingerprinting
- FaceApp
- OSM TagInfo
- OSINT on North Korea
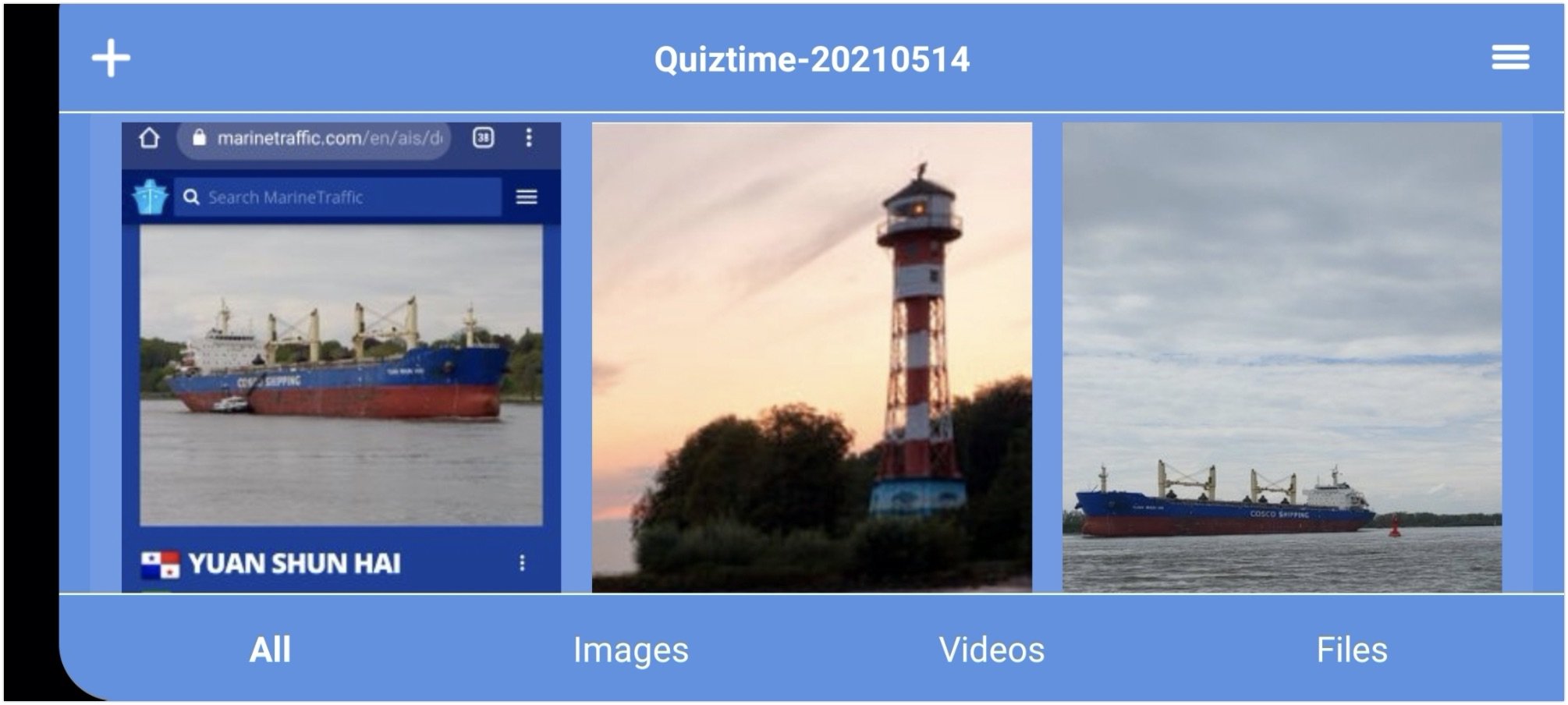
Tool: Hunchly Mobile
Justin Seitz announced a nifty little tool for Android and iOS. Hunchly Mobile enables you to collect certain evidence and create an evidence file, that can be shared with others, or imported into a case file on the desktop version. This for instance enables journalists to let people share content like video footage to be shared with others. I did miss the option to save URL's in the app, especially since I work a lot with digital information from the web. But as a workaround Hunchly tells you to create a screenshot, and you can then easily add the URL in the notes.
iOS: https://apps.apple.com/ca/app/hunchly-mobile/id1566453410
Android: https://play.google.com/store/apps/details?id=com.hunchly
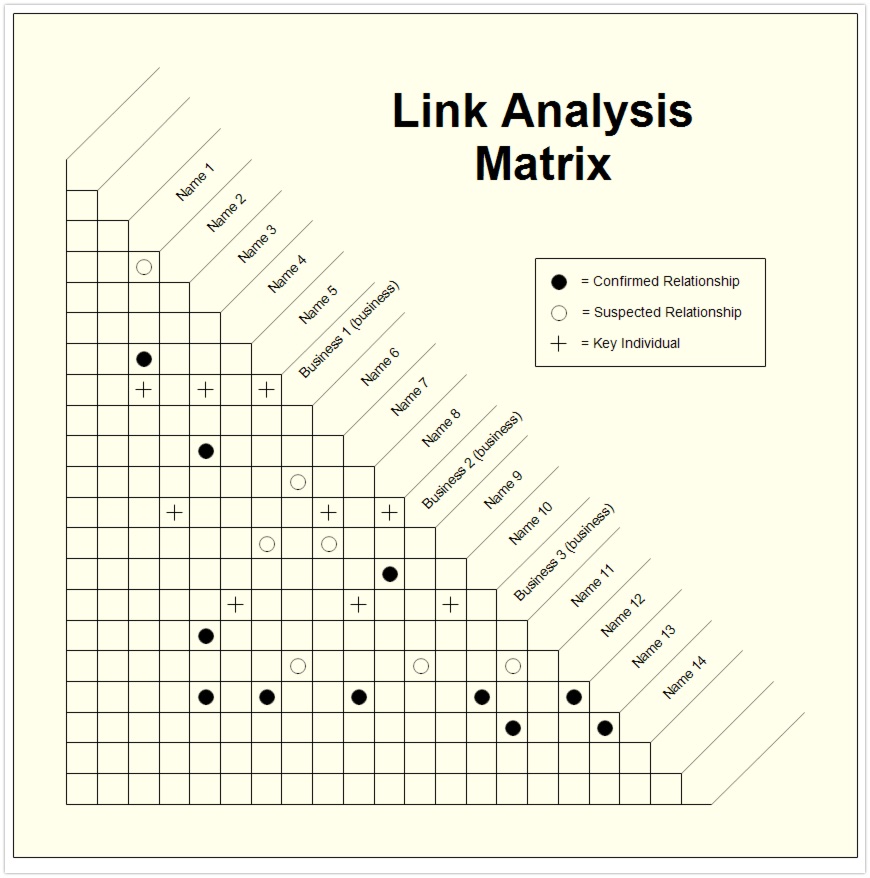
Article: Clint Watts
Shakira on Security shared a link to an interview with Clint Watts, the former FBI agent and executive officer at the CTC. He shares some really useful tips that are applicable to the investigative work that most of you readers are interested in. Good advice like focussing on investigative techniques rather than tools or platforms, and a useful 'Link Analysis Matrix' to get insight in relationships.
Link: https://brackets.substack.com/p/7-life-lessons-from-25-years-in-counterterrorism
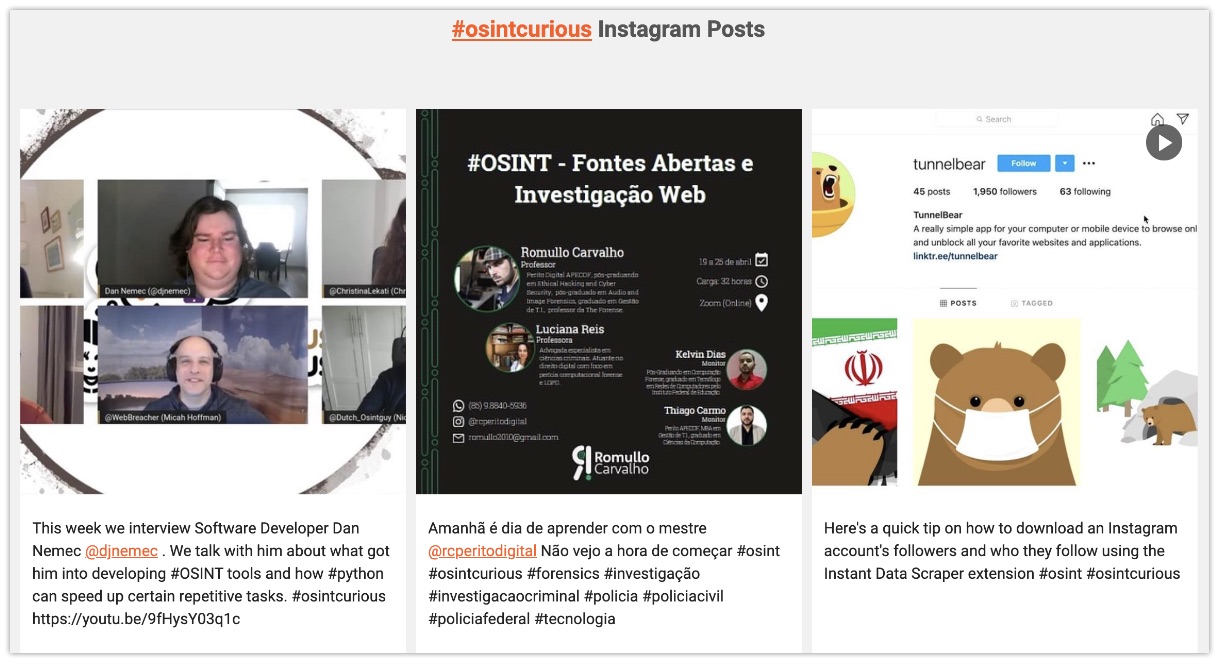
Site: Instagram Tools
Wopita, formerly known as Pictabear, seems to be gone since some time. The website offered a nice way to anonymously browse and search Instagram posts. But '7oaster' and 'nomoredroids' on the SearchLight Discord shared some sites that offer the same functionalities: Dumpor, Pixwox and Picuki. You can search by hashtags, locations or accounts, where Pixwox seems to be the most stable and looks to me it offers more recent content compared to Dumpor and Picuki. Another issue is that Pixwox and Dumpor had issues with showing posts from locations, where Picuki had no issues with that, though it was running half a day behind. So I wouldn't always recommend these sites on a regular basis, but as 7oaster commented: These sites might have archives posts on archive.is or archive.org, making it a good option to find removed posts.
Dumport: https://dumpor.com
Pixwox: https://www.pixwox.com
Picuki: https://www.picuki.com
Tip: Browser Fingerprinting
When you talk to an OSINT expert about staying anonymous, they'll probably tell you about 'fingerprinting' sooner or later. This is where third parties assign a unique identifier to your browser or system, making it possible to track you, even if no cookies are set. The research by FingerprintJS goes beyond that and shows that even with the best OpSec there seem to be methods to fingerprint your systems. Simply by checking what applications are installed on a system. If you need to keep your VM's unique from now on, you'll might have to start thinking about installing a subset of applications, or removing them, to create a fingerprint that might be generic enough to beat this. To check the uniqueness of your browser, there's the website 'Am I Unique'. But they haven't incorporated this technique yet, so they mainly look at OS and browser, screen size, installed extensions, language settings and so on.
We found a vulnerability that allows for cross-browser tracking in Chrome, Firefox, Safari, and Tor. Read our article to learn more about the exploit, and try our live demo for yourself - https://t.co/SKkK2Exz9u#privacy #Chrome #Safari #tor #webdevelopment
— FingerprintJS (@FingerprintJs) May 13, 2021
Link: https://fingerprintjs.com/blog/external-protocol-flooding/
AmIUnique: https://amiunique.org/
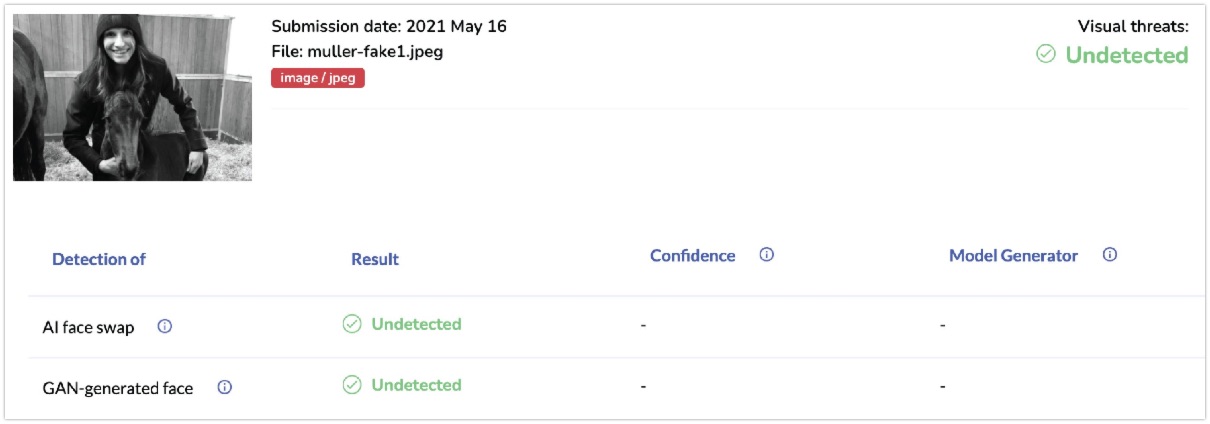
Tip: FaceApp
A nice tip from Matthias, about creating new and almost undetectable faces by using FaceApp. By combining existing photos with the face of someone else, you're able to create a unique photo that might be able to provide you with a nice profile picture of your next sock account.
Need pics of the same person to make your sock puppet more realistic? Why not use FaceApp to alter existing images to change age or gender? If done well, these could withstand a reverse image search (oh, and don’t upload pics of yourself) #OSINT
— MW-OSINT (@MwOsint) May 16, 2021
Now who might this young woman be? pic.twitter.com/RFmZKWHxVa
And even though it might not be perfect, and could use some manual editing to make it even more unique, it does seem to beat some detection mechanisms as OSINTgeek pointed out.
iOS: https://apps.apple.com/us/app/faceapp-ai-face-editor/id1180884341
Android: https://play.google.com/store/apps/details?id=io.faceapp
Site: OSM TagInfo
For people that work with Overpass Turbo, this site might be known already. It's not the OSM Wiki with the different nodes, but it is a database with all the different tags that are available, how many are indexed and their geological placement throughout the world. And the best thing of all is that you're able to open a query in Overpass Turbo on that specific tag with a single click. So if you are looking for a specific tag, you can now quickly estimate whether the area of interest may have them, or whether it's better to use a different tag to narrow your searches.
Link: https://taginfo.openstreetmap.org/
Media: OSINT on North Korea
While browsing around a bit, I found an awesome YouTube channel called SecurityFWD. On this channel you find videos on cybersecurity, hacking and digital investigations, and in this video they have a look into North Korea. Kody Kinzie looks at a domain name with Maltego, pivots on DNS servers, finds breached email addresses and discovers more North Korean websites. Wonderful showcase on how to use Maltego in digital investigations that involve domain names. Except maybe for the part where he runs all transforms after not finding a specific option 😉
Link: https://www.youtube.com/watch?v=oFbfDTBsxK0
Fun: Movie Time!
Sylvain Hajri has created a very, very lengthy thread on Twitter on movies about OSINT, investigations and hacking. Sylvain correctly claims that both OSINT and hacking is about the mindset, not only about skills. And it's true, both work with a visible part of a puzzle, and you're trying to find underlying pieces of information to complete a picture. Whether it's a technical infrastructure, or the verification of a specific event, both require you to work towards unraveling facts that can be used for your purpose.
[THREAD] #Hacking & #OSINT are not just about skills, it's also a mindset!
— Sylvain Hajri (@navlys_) May 13, 2021
Here's a brief list of documentaries/movies/series that I recommend to watch to discover our wonderful domains.
And also to stop my students calling me a boomer😅
Link to Twitter thread: https://twitter.com/i/status/1392941294394253314
Have a good week and have a good search!
